How we protect our users against the Sunburst backdoor


What transpired
SolarWinds, a properly-identified IT managed companies supplier, has just lately turn into a sufferer of a cyberattack. Their solution Orion System, a resolution for monitoring and taking care of their clients’ IT infrastructure, was compromised by threat actors. This resulted in the deployment of a custom Sunburst backdoor on the networks of additional than 18,000 SolarWinds consumers, with several big organizations and governing administration entities amongst the victims.
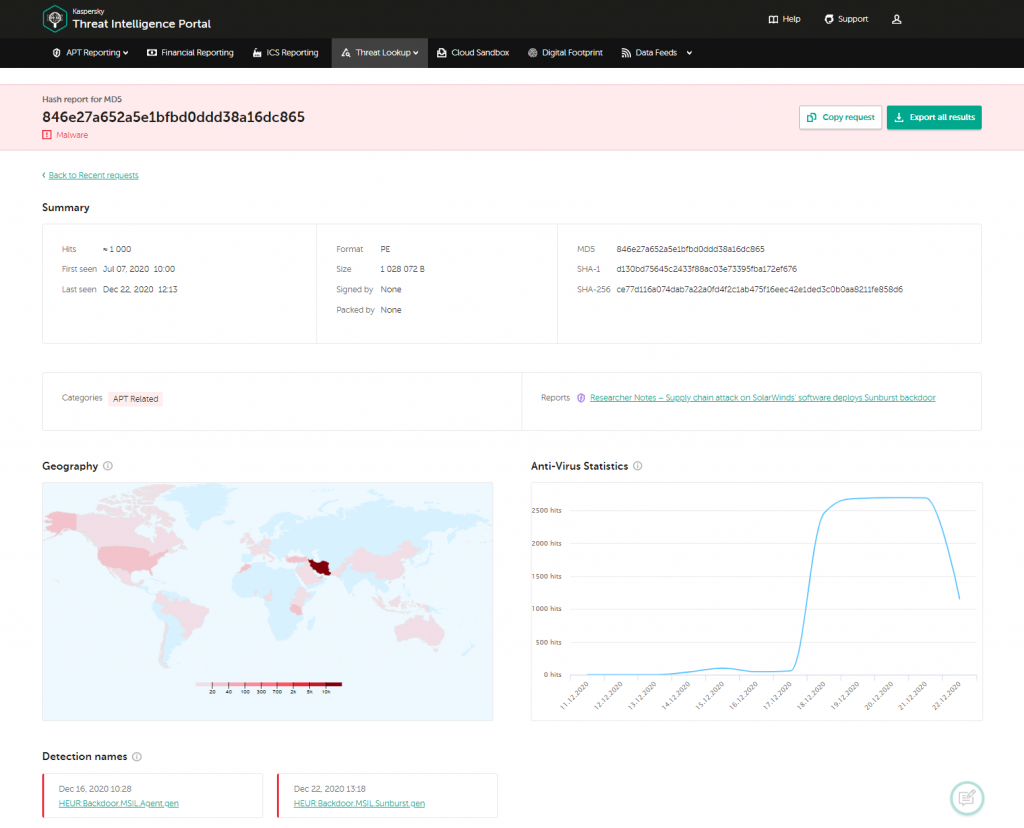
In accordance to our Threat Intelligence data, the victims of this subtle source-chain assault had been found all around the world: the Americas, Europe, Middle East, Africa and Asia.
Right after the preliminary compromise, the attackers seem to have picked out the most worthwhile targets amongst their victims. The organizations that appeared to be of special interest to the destructive actors could have been subjected to deployment of added persistent malware.
General, the proof obtainable to day implies that the SolarWinds source-chain assault was intended in a specialist way. The perpetrators behind the attack made it a precedence to keep undetected for as prolonged as doable: after the set up, the Sunburst malware lies dormant for an prolonged period of time of time, trying to keep a low profile and thwarting automatic sandbox-sort assessment and detection. Moreover, the backdoor makes use of a refined plan for target reporting, validation and upgrading which resembles techniques involved in some other notorious provide-chain attacks.
Examine additional about our exploration on Sunburst malware in this article. Extra experiences and indicators of compromise are accessible to our Risk Intelligence Portal buyers.
How to guard your business versus this risk
The detection logic has been improved in all our alternatives to make sure that our clients remain safeguarded. We carry on to look into this attack using our Threat Intelligence and we will insert further detection logic the moment they are necessary.
Our goods shield in opposition to this menace and detect it with the next names:
- Backdoor.MSIL.Sunburst.a
- Backdoor.MSIL.Sunburst.b
- HEUR:Trojan.MSIL.Sunburst.gen
- HEUR:Backdoor.MSIL.Sunburst.gen
- Backdoor.MSIL.Sunburst.b
Our Conduct Detection part detects activity of the trojanized library as PDM:Trojan.Acquire32.Generic.
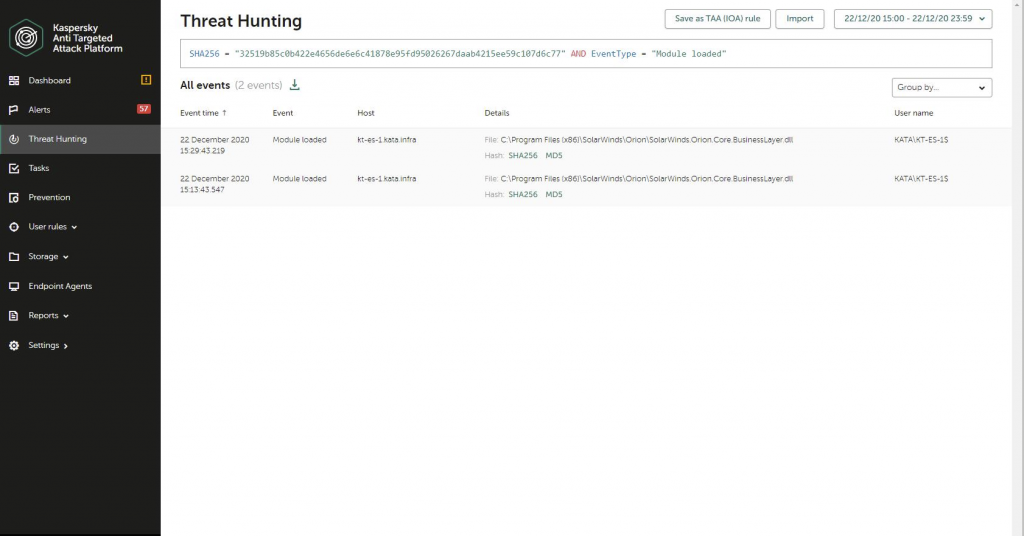
Our Endpoint Detection and Response (Qualified) platform can be handy in seeking for and identifying traces of this attack. The client can lookup for Indicators of Compromise (these as hashes or area names) with an .ioc file or right with the Threat Searching interface:
Or, shoppers can use the IoA Tag, which we have additional particularly for this attack:
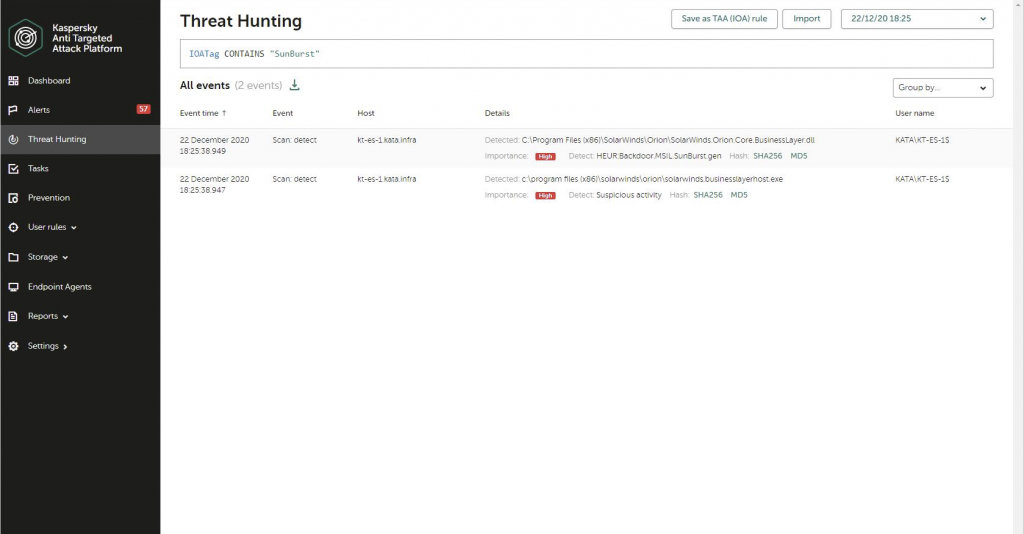
This rule marks endpoint detections for Sunburst to make it a lot more clearly visible to safety officers:
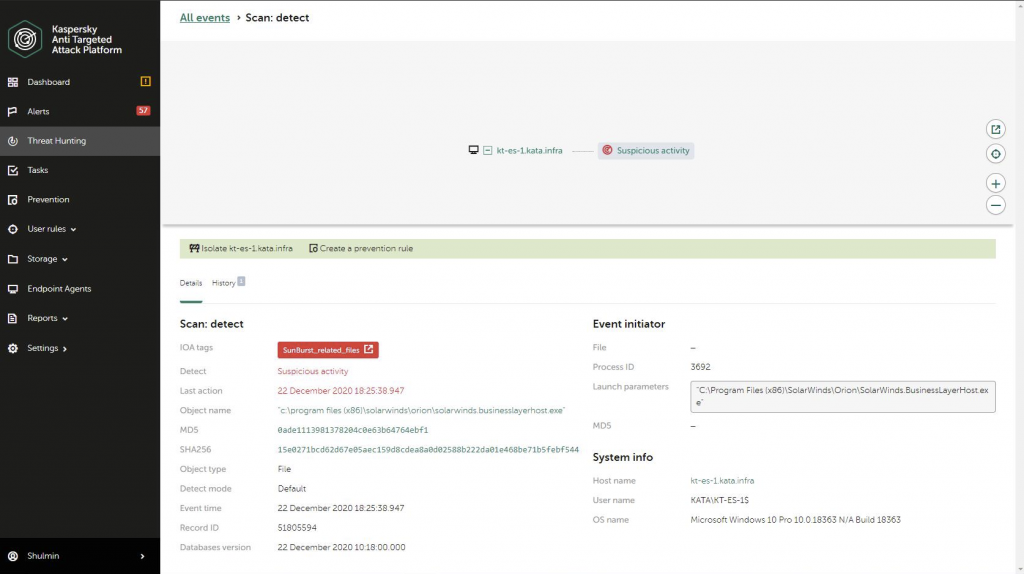
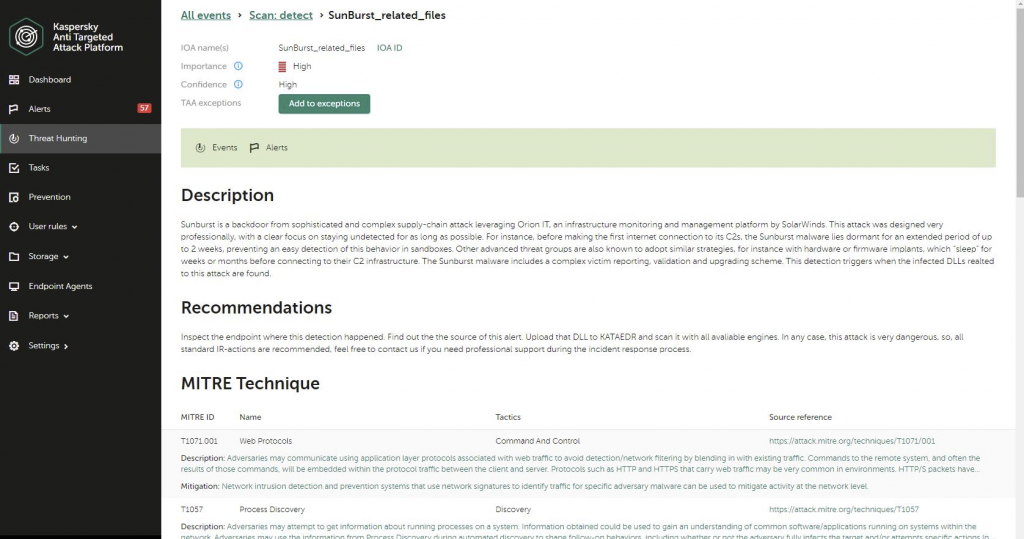
Our Kaspersky Anti-Specific Attack Platform detects Sunburst traffic with a established of IDS guidelines with the adhering to verdicts:
- Trojan.Sunburst.HTTP.C&C
- Backdoor.Sunburst.SSL.C&C
- Backdoor.Sunburst.HTTP.C&C
- Backdoor.Sunburst.UDP.C&C
- Backdoor.Beacon.SSL.C&C
- Backdoor.Beacon.HTTP.C&C
- Backdoor.Beacon.UDP.C&C
Our Managed Detection and Reaction assistance is also ready to determine and stop this assault by using menace searching procedures to spot many actions that can be performed by the Sunburst backdoor as effectively as detections from Kaspersky Endpoint Safety.
Sunburst / UNC2452 / DarkHalo FAQ
- Who is powering this attack? I browse that some persons say APT29/Dukes?
At the moment, there are no complex back links with previous assaults, so it may perhaps be an entirely new actor, or a earlier regarded a single that developed their TTPs and opsec to the place exactly where they can’t be joined anymore. Volexity, who earlier worked on other incidents connected to this, named the actor DarkHalo. FireEye named them “UNC2452”, suggesting an unknown actor. When some media resources joined this with APT29/Dukes, this seems to be either speculation or based on some other, unavailable information, or weak TTPs this kind of as authentic domain re-use. - I use Orion IT! Was I a concentrate on of this assault?
1st of all, we propose scanning your procedure with an up-to-date safety suite, able of detecting the compromised offers from SolarWinds. Test your network targeted visitors for all the publicly recognised IOCs – see https://github.com/fireeye/sunburst_countermeasures. The simple fact that another person downloaded the trojanized packages doesn’t also signify they were being selected as a focus on of fascination and obtained further more malware, or suffered info exfiltration. It would surface, based mostly on our observations and frequent sense, that only a handful of the 18,000 Orion IT clients have been flagged by the attackers as attention-grabbing as were even more exploited. - Was this just espionage or did you notice damaging actions, this sort of as ransomware?
Although the broad the vast majority of the superior-profile incidents nowadays include ransomware or some sort of harmful payload (see NotPetya, Wannacry) in this scenario, it would look the major target was espionage. The attackers confirmed a deep knowing and knowledge of Business365, Azure, Trade, Powershell and leveraged it in many innovative techniques to regularly monitor and extract e-mails from their true victims’ programs. - How numerous victims have been determined?
Several publicly out there facts sets, this sort of as the one particular from John Bambenek, include DNS requests encoding the sufferer names. It really should be pointed out that these victim names are just the “initial phase” recipients, not necessarily the ones the attackers deemed fascinating. For instance, out of the ~100 Kaspersky consumers with the trojanized package deal, it would show up that none had been appealing to the attackers to obtain the 2nd phase of the attack. - What are the most influenced nations?
To day, we observed end users with the trojanized Orion IT bundle in 17 nations around the world. Nevertheless, the complete quantity is probable to be much larger, considering the official figures from SolarWinds. - Why are you contacting this an attack, when it’s just exploitation? (CNA vs CNE)
Sorry for the terminology, we only refer to it as a “provide chain attack”. It would be odd to explain it as a “source chain exploitation”. - Out of the 18,000 first stage victims, how a lot of were being exciting to the attackers?
This is difficult to estimate, mostly because of the deficiency of visibility and since the attackers were actually cautious in hiding their traces. Based mostly on the CNAME data posted by FireEye, we discovered only two entities, a US federal government firm and a telecommunications corporation, who were tagged and “promoted” to devoted C2s for further exploitation. - Why didn’t you catch this offer chain attack in the initially spot?
That’s a superior problem! In certain, two matters produced it genuinely stealthy. The gradual conversation approach, in which the malware lies dormant for up to two weeks, is 1 of them. The other one particular is the lack of x86 shellcode the attackers utilised a .Net injected module. Last but not minimum, there was no important transform in the file sizing of the module when the malicious code was added. We noticed two suspicious modules in 2019, which jumped from the normal 500k to 900k for SolarWinds.Orion.Main.BusinessLayer.dll. When the destructive code was 1st included, in February 2020, the file didn’t change dimensions in a substantial manner. If the attackers did this on intent, to keep away from upcoming detections, then it’s a quite outstanding detail. - What is Teardrop?
In accordance to FireEye, Teardrop is malware delivered by the attackers to some of the victims. It is an unfamiliar memory-only dropper suspected to deliver a tailored model of the very well-recognized CobaltStrike BEACON. To date, we haven’t detected any Teardrop samples any where. - What produced this such a productive operation?
Possibly, a mixture of issues – a provide chain assault, coupled with a pretty properly believed 1st phase implant, careful target selection tactics and final but not the very least, no apparent connections to any earlier noticed TTPs.