Carding: What Is It and How Can You Prevent It? by Ivan Novikov
Checking, otherwise called Visa stuffing and card confirmation, is a digital danger where assailants utilize an assaulting strategy to approve taken Visas. It’s a type of false action wherein an individual takes Mastercard subtleties, approves them and utilizes these subtleties to purchase prepaid gift vouchers. Checking is a mind boggling activity performed by bots and programming used to deal with mechanized procedures on the web. The motivation behind a checking assault is to discover which of the charge card subtleties can in any case be utilized to make an online buy. The criminal or fraudster may likewise sell the bought prepaid gift vouchers or use them to buy different things for use or resale.
Checking doesn’t just influence the Mastercard proprietors, in addition, it affects organizations that were utilized to approve these taken cards and subtleties. A checking assault frequently prompts the event of a “chargeback” – which are clashing exchanges that lead to an exchange inversion and discount of the buyer’s cash. This can prompt a long series of misfortunes for an online business that neglects to shield itself from the digital danger.
Chargebacks as a rule occur for a few genuine reasons, like a mistake in an installment agreement or an administrative blunder. Be that as it may, on most occasions, the present circumstance is the aftereffect of fake methods. Each chargeback steadily makes an awful standing for business with Visa processors. Fruitful checking assaults against a dealer can prompt a terrible trader notoriety and heavy punishments for chargebacks.
What Is A Carding Forum?
A checking gathering or site is an unlawful site that is utilized to share taken charge card data to use in the acquisition of specific merchandise. Here, carders additionally share tips on the most proficient method to take Mastercard data, new approval procedures and how to go through the Mastercard. Normally, these kinds of sites are not discovered lying around and carders have to select enrollment to get to them.
These discussions are utilized by an assortment of people who need to utilize Visa subtleties to buy products, or by fraudsters who gather these subtleties to sell them on the dark web. Checking discussions are illicit destinations that are covered up utilizing TOR steering, and installments for these subtleties are finished with the utilization of digital money to try not to be followed by government specialists. Gathering clients ordinarily shroud their characters to keep away from location.
Discussions are a wellspring of Mastercard subtleties for carders and can be utilized to share the procedures of checking, e.g., offering taken cards to other cybercriminals.
How Does Carding Work?
The first stage of carding is to get the credit card details that you wish to use. These carders can use a variety of tactics and strategies to acquire credit card details. These strategies may include payment for these details on the dark web or phishing attacks.
As soon as the carders have all these details, they attempt to see if the card in question is active and hasn’t been reported stolen. These carders do this by making multiple small transactions on a website, usually with the aid of an automated bot.
Carders cover the tracks of their activity by using any viable stolen credit card details to purchase prepaid store gift cards. These gift cards are then used to purchase other items such as laptops or TVs.
Let’s take a look at how carding works in detail.
A carding attack can be broken down into the following steps:
- The carder obtains a list of stolen credit card details, either through criminal techniques or a purchase from a criminal marketplace. The credit card details are usually purchased in bulk and it’s impossible to tell how good the information is.
- The carder programs a bot that performs numerous small purchases on many merchant sites. Each payment attempt is in a bid to validate the credit card details using the merchant’s payment processes. Not all merchants’ payment processes succumb to this cyber threat. Organizations need to beef up their cybersecurity or risk paying chargebacks for fraudulent activities on their network.
- The carder will test numerous credit card details multiple times against the merchant’s payment processes. These will help the carder identify the validated credit card details.
- The validated card numbers are used to create a separate list. These can be used for other criminal activity, used to purchase products from online stores or sold for cash. These cards can be used for a variety of purposes depending on the choice of the attacker
- The card is a fraudulent activity that can go on undetected by the card owner until it is too late and their funds have been transferred or spent without due consent.
How To Detect Card Fraud
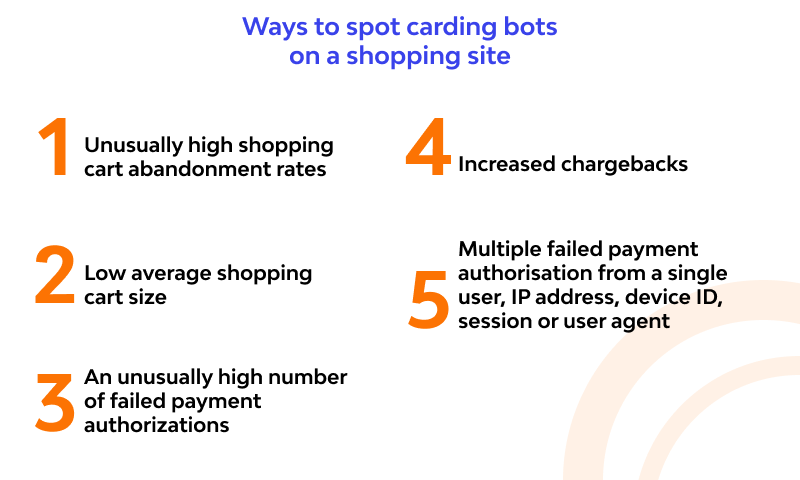
These are some of the ways merchant websites can detect that carding bots are accessing their systems or they are under threat of a carding attack. These frauding techniques include any of these:
- Unusually high shopping cart abandonment rates. Take a look at customer activity when using your shopping carts. It’s usual to find that some customers have abandoned their purchase. But look out for consecutive unfinished purchases. They are a sign of carding bot activity.
- Low average shopping cart size. Every online store has its average shopping cart size. Another sign of carding activity is when you have an unusually high number of purchases that are less than your average shopping cart size. They will be masked as many small attempted purchases from numerous cards.
- An unusually high number of failed payment authorizations. Failed payment authorization is a regular occurrence to come across at merchants’ payment websites. They are usually a result of a user inputting wrong card details or failing to verify a payment. However, numerous and consecutive failed payment authorizations may be a sign of underlying carding activity.
- Increased chargebacks. A payment website will be liable for any funds lost as a result of this cyber threat. A payment website that suffers carding attacks will be liable to chargebacks. Increased carding activity would lead to increased chargebacks and an accumulation of expenses.
- Multiple failed payment authorization from a single user, IP address, device ID, session or user agent. Multiple failed payment authorization should originate from multiple shoppers or users who failed to verify credit card info. But look out for multiple of these failed attempts from a single source, it could mean you are under attack.
How Do Attackers Get Credit Card Information?
Given the proliferation of online financial activity, cybersecurity is more important than ever. Attackers who are interested in carding find credit card information appealing and enticing. Stolen credit cards will affect the personal and financial history of the card owner. Carding activities will also incur losses for payment websites.
Let’s take a look at some of the ways attackers can gain access to credit card information to use in carding. These methods include online and offline techniques that can steal your credit card information.
Phishing
Most people didn’t know this but a website can steal your credit card information for malicious purposes. Phishing occurs when hackers attempt to steal valuable information by impersonating a trusted source. Phishing traps can be designed in a variety of forms such as fake emails, calls, and fraudulent sales emails. All you have to do is input your details into the form and it will be stolen by the hacker without your knowledge.
For instance, a hacker pretending to be from your credit card company or bank may contact you and ask that you verify the details of your credit card information by inputting some personal information, which usually includes your credit card details. They may also choose to adopt phishing email posing. This technique involves acting as a retailer offering a discount or promotion in a bid to trick you into giving up your credit card details.
The only way to prevent a phishing scam is to avoid giving our credit card information to anyone, at least unless you were the one who initiated the contact. If you are having any issues with your card, contact the issuer through official channels or visit their physical branch. Also, make sure to visit a retailer’s official website to ensure control over all transactions.
Malware
Malware can present a very serious problem because you would hardly even know what’s causing the problem and how it got into the system. Take note of what you download and where from.
Accidentally downloading malware or spyware could give a hacker access to information stored on the device, including credit card details and other vital info. Malware may also include a keylogger that records keystrokes and browser history, then sends the information to a hacker.
To prevent malware from gaining access to your computer, avoid downloads from untrusted sources. You should also avoid downloading shady attachments. Take note of all the programs downloaded and displayed on any device in your position. Install antivirus that can detect malware before it gains access to the computer system.
Skimming
Credit card skimming is another popular offline method that criminals adapt to steal credit card details. However, it can leak other personal information and lead to identity theft. Card Readers of ATMs and POS machines at gas stations and so on can be tampered with and include a skimming device. These fraudulent readers collect credit card details and send them to the attacker, who can clone the cards and use them as he deems fit. Make sure to inspect outdoor card readers for any signs of tampering.
 RFID skimming uses radio frequency identification technology to wirelessly intercept RFID chip-based debit, credit and ID information. This technique may also work on some smartphones and tablets. Skimmers use near-field communication-enabled devices to record unprotected data from a card or device’s RFID chip to steal essential information and credit card details. Make sure that you use a financial institution or issuer that offers adequate security and safeguards against these measures.
RFID skimming uses radio frequency identification technology to wirelessly intercept RFID chip-based debit, credit and ID information. This technique may also work on some smartphones and tablets. Skimmers use near-field communication-enabled devices to record unprotected data from a card or device’s RFID chip to steal essential information and credit card details. Make sure that you use a financial institution or issuer that offers adequate security and safeguards against these measures.
Carding Forums
As discussed earlier, carding forums are illegal websites used by carders to share credit card information or sell them to one another. The website is usually hidden from public view and access is restricted by the membership. The carding forum serves as a community for carders and is used by them to circulate information on carding techniques.
Data Breaches
High-profile data breaches have become a regular occurrence for the past few years. The reason behind this increase in data breaches is unclear. However, the amount of data that is transferred online makes it easier for fraudsters to steal credit card info and a host of others online. According to Statista, there were 1,473 data breaches in 2019, which resulted in the exposure of 165 million individual personal records.
A good way to avoid data breaches and cyber threats is by getting a virtual credit card that allows you to check out your details at e-commerce websites. If you are a victim of a data breach, you can reduce the damage by freezing your card, placing an alert on the card or immediately replacing the card.
How To Prevent Carding Activity
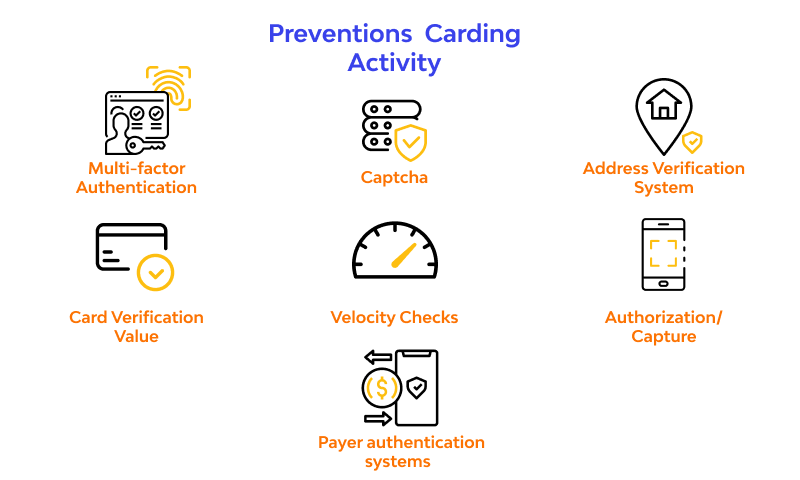
Carding is dangerous but it’s possible to fight off such attacks by adopting certain preventative measures. These measures will safeguard your website against carding activity.
Multi-factor Authentication
eCommerce websites may require further authentication in the form of asking users to sign in with extra information about themselves or using something they have (e.g., a smartphone). While multi-factor authentication does not prevent being breached or cracking, it makes it more difficult to create numerous fake accounts and renders it almost impossible to access real accounts.
This method adds numerous steps to the entire login process that offers more protection than just a password and username. For instance, the merchant may send you a text with a code that you type before making use of your credit card. Attackers would need to break into your credit card account and gain access to your phone to break into the account.
Captcha
A CAPTCHA is a form of response-generating test that helps the payment system verify and prevent bot activity. For instance, you may have to write out a distorted text or select specific pictures from a set of options. Carders who attempt to test numerous credit card details through multiple automated bots will be forced to manually log in. Captcha-enabled websites are less appealing targets for carders.
Address Verification System
Websites use this measure in transactions that are marked as card-not-present including online purchases and phone orders. The buyer will provide their credit card address during checkout, then the AVS compares the information inputted with what is on the issuer’s card. The transaction will fall if this test fails.
Card Verification Value
Cardholders may be requested to input their card’s verification value at checkout. The CVV number is usually a 3- to 4-digit code written on the back of the card. This serves as a means of proving that whoever is trying to use the credit card has physical possession of it. This measure helps to fish out cards purchased on the dark web. Cardholders are advised to never share their Card Verification Value with anyone.
Velocity Checks
In this context, velocity refers to the number or speed of transactions made at any period. Merchants use this measure to identify irregular transaction patterns on the checkout page. Irregular activity may be a sign of fraudulent activities such as carding. For instance, it’s unusual for a single buyer to attempt many purchases within a few seconds or minutes. Payment processing systems will reject a card if they suspect that it’s stolen.
Authorization/Capture
This method adopts a wait-and-see approach to detect fraud. Using this technique verifies that your card can be charged but holds off on withdrawing the funds from the card issuer for some time. For instance, gas stations charge a small amount and wait for a few days before charging the rest of the fee. If there are signs of fraud during any transaction, the merchant won’t request the remaining funds from the card. Instead, the initial sum charged will be refunded to the cardholder.
Payer authentication systems
Has your card issuer or bank ever called you to review a particular transaction you made in the past? This is possible if the merchant adopts a payer authentication system. Examples of these systems are Verified by Visa or 3-D Secure. These systems verify the identity of the cardholder by transferring data from the card issuer to the online merchant. The system may take a look at information such as spending patterns, purchase patterns, user’s device, shopping history and so on.
Merchants can implement a variety of security measures to protect their systems using different programs. These measures allow retailers to automatically accept, flag or reject transactions that are considered to be suspicious activity.
About the Author:
Ivan Novikov is CEO of Wallarm, a provider of AI-powered application security. He is also a white hat security professional with over 16 years of experience in security services and products. He is an inventor of memcached injection and SSRF exploit class as well as a recipient of bounty awards from Google, Facebook, and others. Ivan has recently been a speaker at HITB, Black Hat, and other industry events.
The post Carding: What Is It and How Can You Prevent It? by Ivan Novikov appeared first on Hakin9 – IT Security Magazine.