What is PCI? Compliance, Certification and Requirements by Ivan Novikov
PCI COMPLIANCE AND CERTIFICATION
In today’s world of banks and liquid cash flows, numbers and information are worth more than they used to be. For instance, to make transactions from your bank account, you need a combination of codes and specific numbers, then you need a card (or sometimes not). How then have they been able to secure these systems from total collapse because of forgery? What are the principles that help maintain the uniqueness and safety of our transaction cards and, by extension, the key numerals that are on them?
You know, from the surface value, cards just have numbers and pins. Definitely, criminals would have attempted number and identity duplicity; people attempt credit and debit card frauds all the time. However, there is an integrated system that helps maintain the integrity of these cards and numbers and their underlying structure. Who are the individuals responsible for the initiation and regulation of safety in the card? How have the cards been in sync with banks and various financial institutions?
The PCI (payment card industry) is an integration of all the organizations that are involved in storing, transmitting, and processing the data sets of cardholders, especially in the case of debit and credit cards. The integration of these bodies and the synchronization of their services have brought about an almost impregnable card security system. With that, let’s examine the concept of PCI DSS.
WHAT IS PCI DSS?
PCI DSS is an acronym for Payment Card Industry Data Security Standard. It is a set of security standards set up by big companies in the payment card industry and censored by PCI SSC (Payment Card Industry Security Standards Council). The purpose of these security standards is to safeguard cards and card transactions from theft, forgery, and fraud.
These standards were set in 2004 by Discover Financial Services, American Express, JCB International, MasterCard, and Visa. The primary aim of the security standards is to increase the limits to which external parties have access to cardholder data. In essence, all organizations have to follow the set down standards on the intensity and method of protecting cardholder details and cards themselves.
These security standards bound all organizations involved with card transactions globally, from banks to online markets to fintech organizations and so on. Aside from determining the method of protecting cardholder data, it also sets precedence for the manner in which all organizations process card data, from the collection to the transfer and the transactions. With stringent laws on cardholder data came fewer security cracks for criminals to exploit and less exposure of user data.
Due to the scope of PCI DSS, it is an integral part of the success of web applications (especially the ones with an integrated payment system). In the same vein – and as expected – these security standards wield a considerable influence on the structure and design of a web application’s database. By implication, the success of adapting to the standards is largely dependent on proper database management and cyber security principles.
PCI DSS CERTIFICATION
As the body meant to censor data security standards of payment card industries, the SSC lays down a set of requirements that your organization must pass before it is certified to be safe for card-based financial transactions. The ripple effect of this is not one-sided; both the users and the organizations benefit from it. The users feel safe and secure using the services of your PCI-compliant organization. In the same vein, it is a huge boost to your reputation and your overall brand image.
To put that in perspective, try to imagine the implications of losing data and money to cyber criminals on a platform in today’s dispensation. Aside from financial implications, the ripple effect of lost trust can shut down the operations of the organization involved.
Due to the fact that people hold their data, safety, and money security in high regard, it is a necessity that any organization is compliant enough to be certified by the SSC. The certification creates the bedrock of trust needed to facilitate functional financial operations.
You may be curious as to what the criteria for certification are! An organization that passes these requirements is labeled to be PCI DSS compliant. However, you need to understand the level of DSS compliance – as bedrock knowledge – before attempting to work on the available criteria.
PCI DSS COMPLIANCE
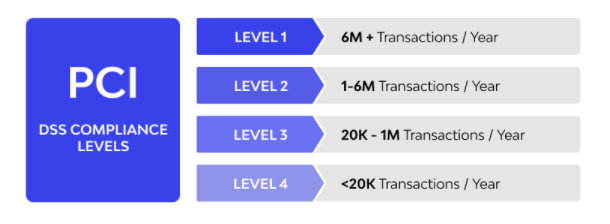
There are a variety of factors that determine whether an organization is PCI DSS compliant. For the sake of structure and clarity, compliance is broken down into four levels. This breakdown is dependent on the number of transactions (either debit or credit) that an organization processes. These levels are the pointers to the minimum pass mark for an organization to remain in compliance.
So, what do the levels of PCI DSS compliance entail?
- LEVEL 1 – This is the peak of the PCI DSS levels. Organizations in this level process more than six million transactions per annum. By the tenets of the PCI DSS, they must conduct an in house audit once a year. This audit must be conducted from a PCI auditor that has authorization. Aside from that, they must submit a properly conducted PCI scan to the SSC once every four months. This PCI scan must be conducted by a scan vendor that is accredited and approved by the SSC.
- LEVEL 2 – This is the second range of organizations. Depending on the circumstances and the judgment of the SSC, these organizations may be required to submit a PCI scan conducted by an approved scan vendor once every four months. Organizations that fall within this category process between one million and six million transactions on an annual basis. One thing is, however, compulsory for these sorts of organizations, they must conduct an annual assessment using an SAQ (self-assessment questionnaire).
- LEVEL 3 – These organizations process within the ranges of twenty thousand to one million e-commerce transactions on an annual basis. Depending on the situation, they may be required to also submit a PCI scan to the appropriate structures. Like organizations in the second level, they must also conduct a self-assessment using an SAQ.
- LEVEL 4 – This is for organizations below the twenty thousand e-commerce transaction landmark. They also may be required to submit a PCI once in four months.
However, like the others, a self-assessment using an SAQ is compulsory.
WHAT ARE THE REQUIREMENTS FOR PCI DSS COMPLIANCE?
Now that you are armed with the background information, let’s dive right into the safety criteria you have to meet to merit a PCI DSS certification.
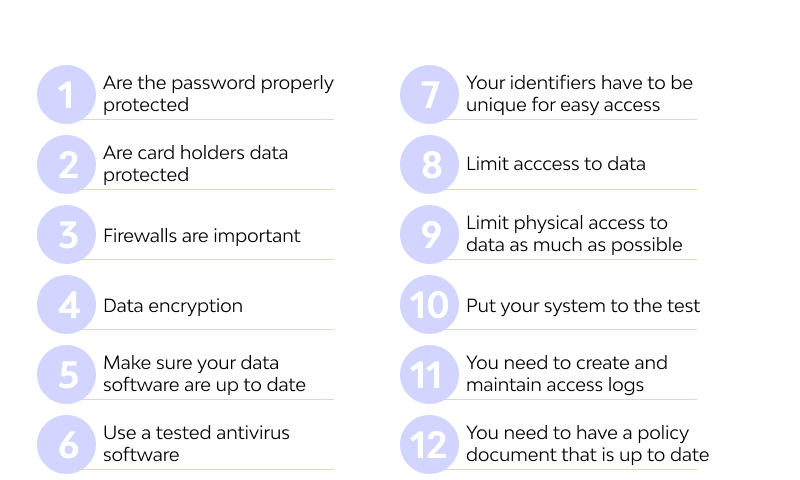
- ARE THE PASSWORDS PROPERLY PROTECTED? – Password protection is one of the fundamentals of data protection. When passwords are exposed, attackers may have access to just the right amount of information necessary to execute theft through cards. The SSC doesn’t specify which method to use. Of course, that is dependent on a lot of factors; however, the organization has to use a tested method that will provide optimal security before certification.
- ARE CARD HOLDERS’ DATA PROTECTED? – A credit card is as safe as the data of the owner. For you to be certified as a PCI DSS compliant organization, your database has to be attack-proof. You must have had a tested cyber security system and a functional recovery and damage control system just in case of a loophole.
- FIREWALLS ARE IMPORTANT – Firewalls are necessary for compliance certification. Your database system has to have a solid firewall system that secures your cardholder database server.
- DATA ENCRYPTION – Card holder data and transaction details have to be encrypted end to end to prevent external access during data movement. This is one of the compulsory requirements of any organization – irrespective of the scale of operation – to get certified.
- MAKE SURE YOUR DATA SOFTWARE ARE UP TO DATE – Every software update has new fixes to security loopholes. Cyber-attacks are more effective when launched against outdated software; they are more likely to be loopholes to exploit when compared to new versions
- USE A TESTED ANTIVIRUS SOFTWARE – One of the major means of executing database attacks is to use malware (like Trojan) to breach the database security. The organization must have working antivirus software in place to forestall any breach that may threaten cardholder data.
- YOUR IDENTIFIERS HAVE TO BE UNIQUE FOR EASY ACCESS – In many instances, you do not necessarily have to give out data to attackers for them to get access to a cardholder’s finances. Some key identifying factors are enough to give the data and the owner out. To protect the cardholder, you have to use a unique and specific identifier to prevent third parties from deciphering.
- LIMIT ACCESS TO DATA – In your organization, you cannot always judge the intent of the insider. Your workflow has to be structured in such a way that the minimum number of people required for effective processing have access to the data. In essence, any individual that doesn’t necessarily need to get access to data (and that can be bypassed) should be removed from the data movement cycle. Once the PCI SSC judges your organization to have the optimal safety structure, you can get certified
- LIMIT PHYSICAL ACCESS TO DATA AS MUCH AS POSSIBLE – As much as you can, try to limit physical access to cardholder data. As part of your cardholder safety procedure, advise the cardholders to limit exposing their card details to outsiders. As an organization (especially a financial institution), your handling of cards should be done in a way with limited exposure to third parties. When the SSC judges that you follow these standards, you can get PCI compliant certification.
- PUT YOUR SYSTEM TO THE TEST – Your system has to pass vulnerability tests before it can be certified to be safe for cardholder data. It has to be tested for reaction to attacks, for possible loopholes and efficiency of the damage responses. Once your cyber security system passes these tests, you can get your DSS certification.
- YOU NEED TO CREATE AND MAINTAIN ACCESS LOGS – An access log is a list that contains all the requests made for user information (whether by bots or humans). If as an organization, you intend to maintain surveillance of cardholder data movement, you need to create a good access log and maintain it. That way, you will be on the lookout for irregular data movement. If you have this, it means you are DSS compliant.
- YOU NEED TO HAVE A POLICY DOCUMENT THAT IS UP TO DATE – A policy document highlights your organization’s stance on data privacy, your approach to data safety and the extent to which you can be held legally accountable. It is very important if you are to get a certification for PCI DSS compliance. It is like a means to gauge your readiness and cover your bases. Finally – for obvious reasons – you need to update it on a regular basis.
ADVANTAGES OF PCI DSS COMPLIANCE
What exact purpose do these standards serve to the cardholder and the organization?
- AS AN ORGANIZATION, YOU GET TO THE TRUST OF YOUR USERS – As mentioned earlier, users like to know that they, their money, and their transactions are safe. The fundamental way of building trust with them is to have the evidence that you are up to the task of keeping them safe. Users definitely feel at rest when they know they can make transactions fast, easy and safe.
- THE USERS AND THE ORGANIZATION ARE FINANCIALLY SAFE – The major aim of DSS is to prevent theft and forgery of card information. Ensuring PCI DSS compliance is a sure way to guarantee that both the organization and the users are protected from these vices. By attempting to meet the requirements, you are actively creating the foundation for a strong database security system.
- EVEN THOUGH YOU MAY NOT KNOW IT, IT HELPS YOU TO SHUT OUT DATA BREACHES – Considering the sort of requirements needed for PCI certification, data breaches are not very feasible. The major goal initially is to fortify your database against data loss. Knowing the implication of data loss on a company’s operation, and the possible catastrophe of data getting into the wrong hands, PCI compliance is definitely worth the hype.
- YOUR ORGANIZATION MEETS GLOBAL STANDARDS – PCI DSS are not just some standards for safety. They are the global litmus for measuring data safety in terms of card transactions. Getting a globally recognized certification would look good for your brand image, don’t you think?
- SETS A FOUNDATION FOR OTHER DEVELOPMENTS – The workload of a big database security plan may look daunting at first. However, little beginnings like PCI DSS certifications create a groundwork that makes it easy to work towards the others.
HOW DOES PCI COMPLIANCE RELATE WITH WEB APPLICATION FIREWALLS?
There is no guaranteed way to keep out attacks totally from a database; even the strongest database systems experience attacks. Since the introduction of PCI DSS in 2004, both attacks and defense of cardholder database systems have evolved. Considering the introduction of fintech companies and the digitalization of banking, the PCI had to come in with a new development to secure card transactions and cardholder information on web applications.
In 2008, a new requirement – for the evolution of digital finance security – was introduced. Complex web application attacks such as DDOS attacks, SQL injections and other basic malware prompted the SSC to take this initiative. This consequently led to the introduction of web application firewalls or manual web code reviews.
The latter is much more time-consuming and prone to human mistakes. It is some sort of vulnerability assessment that requires mechanically scanning through the written code. It is often best done by a third party and it is approved by an expert organization outside the owners of the web application.
Web application firewalls on the other hand are designed to analyze incoming traffic – based on a predetermined algorithm – and filter potential dangers out. This firewall exists between the application in question and the users. Web application firewalls are constantly placed under checks by administrators to conform to the latest happenings in the cyber security space. After a specific period of time, the firewall is optimized to handle even newer versions of potential threats.
SUMMARY
- The PCI is responsible for the smooth integration and safety of the cardholder and the financial institution.
- They have been able to achieve this through the introduction of the Payment Card Industry Data security standard.
- Organizations are at certain levels and expectations based on the SSC classification spectrum. The difference is based solely on the difference in the amount of card transactions they make on an annual basis.
- There are quite a number of requirements that organizations have to meet if they are to get certified by the PCI for being compliant. These may include database security, policy documents and the range of third party access to data.
- Due to the introduction of digital banking, the web application firewall (WAF) was developed to keep dangerous traffic out through algorithm based filtering.
About the Author:
Ivan Novikov is CEO of Wallarm, a provider of AI-powered application security. He is also a white hat security professional with over 16 years of experience in security services and products. He is an inventor of memcached injection and SSRF exploit class as well as a recipient of bounty awards from Google, Facebook, and others. Ivan has recently been a speaker at HITB, Black Hat, and other industry events.
The post What is PCI? Compliance, Certification and Requirements by Ivan Novikov appeared first on Hakin9 – IT Security Magazine.