UhOh365 – A Script That Can See If An Email Address Is Valid In Office365 (User/Email Enumeration)

A script that can see if an electronic mail handle is legitimate in Business365. This does not accomplish any login attempts, is unthrottled, and is unbelievably valuable for social engineering assessments to come across which emails exist and which do not.
Microsoft does not take into consideration “e-mail enumeration” a vulnerability, so this is having advantage of a “element”. There are a few other public Office365 e mail validation scripts out there, but they all (that I have witnessed) have to have at least 1 login attempt for every consumer account. That is detectable and can be uncovered as a light bruteforce attempt (1 “widespread” password throughout many accounts).
This script will allow for e-mail validation with zero login makes an attempt and only employs Microsoft’s crafted-in Autodiscover API so it is invisible to the particular person/corporation who owns the e-mail deal with. Also, this API contact appears to be wholly unthrottled and I was equipped to validate about 2,000 electronic mail addresses in 1 moment in my tests.
Use
The script is in fact really primary and quick to use. You make a file of the e-mails you want to see are legitimate or not and pass it as an argument to the script. Or you can present a file just of usernames and give the -s argument to instantly append a suffix to each individual entry:
Use: UhOh365.py [-h] [-v] [-t THREADS] [-o OUTPUT] file
positional arguments:
file Input file made up of just one e-mail per line
optional arguments:
-h, --support exhibit this assist information and exit
-v, --verbose Show just about every outcome as valid/invalid. By default only displays legitimate
-s, --suffix Insert a domain suffix to each and every input line from file (e.g: contoso.com)
-t THREADS, --threads THREADS
Selection of threads to run with. Default is 20
-o OUTPUT, --output OUTPUT
Output file for legitimate emails only
-n, --nossl Change off SSL verification. This can boost speed if
wanted
-p PROXY, --proxy PROXY
Specify a proxy to run this through (eg: 'http://127...1:8080')
Rationalization
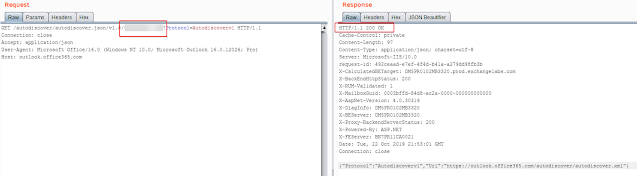
This is truly a pretty straightforward detail to do. It turns out the /autodiscover/autodiscover.json/v1./Electronic mail?Protocol=Autodiscoverv1 API endpoint returns different position codes for if an email exists in o365 or not. 200 standing code indicates it exists, a 302 usually means it won’t exist.
Recognize this ask for will take zero authentication or identifying parameters and it does not cause a login attempt on the concentrate on account.
Writer
Chris King
@raikiasec