SIRAS – Security Incident Response Automated Simulations

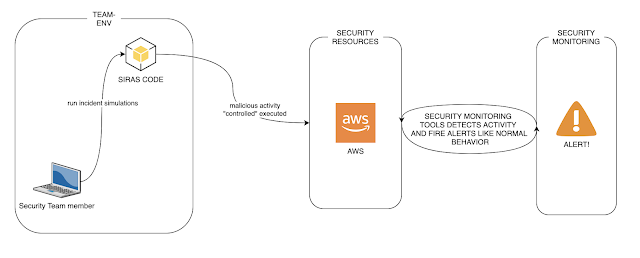
Security Incident Response Automatic Simulations (SIRAS) are inside/managed steps that give a structured chance to observe the incident reaction program and techniques in the course of a sensible scenarios. the major strategy of SIRAS is develop an detection-as-a-code screening eventualities to aid the blueteam/tabletops situations. All smokers of siras make authentic steps into your AWS and then delete those people steps in the same execution.
SIRAS is the incident response pal when you will need to check your controls/alerts 🙂
Why SIRAS?
Currently, the incident detection and response group are acquiring differents mechanisms to avert/detect quite a few varieties of incidents, leaving aside the test stage. Though each inform/automation is examined in advance of employing it, and it is not frequently monitored. For this, SIRAS proposes an automated exam product wherever it is expected to set off alerts in a managed way to make security incidents simulation.
How to run:
1- ACTIVATE VIRTUALENV
virtualenv siras && resource ./siras/bin/activate2- GET Assist
python3 siras.py -s examinationChoices TO Operate (desired)
-s for the “smoker”
| -s | Description |
|---|---|
| all | run all smokers. |
| exam | examination siras if functions. |
| sg | Make an open up sg into AWS and nuke it. |
| pa | Several auth failed into vpn paloalto portal (please config “pano_url” into smoker/PanAuthSmoker.py) |
| au | Generate an adminsitrator person into AWS. |
| aca | Various auth unsuccessful into AWS console portal (you should config “account_id” into smoker/awsConsoleAuthSmoker.py) |
| ctr | Make and delete a cloudtrail path loggin. |
| s3p | Generate an s3 bucket community. |
| esb | Produce an esb general public snapshot (please config your snapshot ID into smoker/EBSPublicSmoker line27) |
Selections TO Run (optional)
| -b (to run) | Description |
|---|---|
| Accurate | help save success into s3-bucket. |
| Bogus | This is the default, just print the output into the console |
Requeriments
- Python
- VirtualEnv
- AWS Credentials
- ENV identify ‘BUCKETS3’ to help save the logs into that bucket if “accurate”.
- (If you dont want to use virtualenv) pip to put in requeriments.txt
Foreseeable future Integrations
- Kubernetes people who smoke
- VPC variations
- EC2 Infected Smoker.
- GuardDuty Alterations.
Request New Modules/Publish
Make sure you truly feel free to publish or request new modules or use situations, open up a Situation into the repo or make a PR.