Qu1cksc0pe – All-in-One Static Malware Analysis Tool
This tool allows you to statically analyze Windows, Linux, OSX executables and APK files.
You can get:
- What DLL files are used.
- Functions and APIs.
- Sections and segments.
- URLs, IP addresses and emails.
- Android permissions.
- File extensions and their names.
And so on…
Qu1cksc0pe aims to get even more information about suspicious files and helps user realize what that file is capable of.
Usage
python3 qu1cksc0pe.py --file suspicious_file --analyze
Setup
Necessary python modules:
puremagic=> Analyzing target OS and magic numbers.androguard=> Analyzing APK files.apkid=> Check for Obfuscators, Anti-Disassembly, Anti-VM and Anti-Debug.prettytable=> Pretty outputs.tqdm=> Progressbar animation.colorama=> Colored outputs.oletools=> Analyzing VBA Macros.pefile=> Gathering all information from PE files.quark-engine=> Extracting IP addresses and URLs from APK files.pyaxmlparser=> Gathering informations from target APK files.yara-python=> Android library scanning with Yara rules.prompt_toolkit=> Interactive shell.
Installation of python modules: pip3 install -r requirements.txt
Gathering other dependencies:
- VirusTotal API Key:
https://virustotal.com - Binutils:
sudo apt-get install binutils - ExifTool:
sudo apt-get install exiftool - Strings:
sudo apt-get install strings
Alert
You must specify jadx binary path in Systems/Android/libScanner.conf
[Rule_PATH]
rulepath = /Systems/Android/YaraRules/
[Decompiler]
decompiler = JADX_BINARY_PATH <-- You must specify this.Installation
- You can install Qu1cksc0pe easily on your system. Just execute the following command.
Command 0:sudo pip3 install -r requirements.txt
Command 1:sudo python3 qu1cksc0pe.py --install
Scan arguments
Normal analysis
Usage: python3 qu1cksc0pe.py --file suspicious_file --analyze
Multiple analysis
Usage: python3 qu1cksc0pe.py --multiple FILE1 FILE2 ...
Hash scan
Usage: python3 qu1cksc0pe.py --file suspicious_file --hashscan
Folder scan
Supported Arguments:
--hashscan--packer
Usage: python3 qu1cksc0pe.py --folder FOLDER --hashscan
VirusTotal
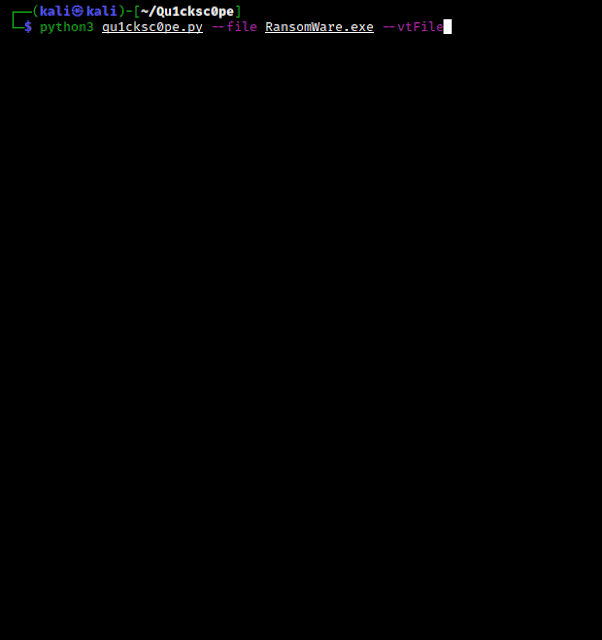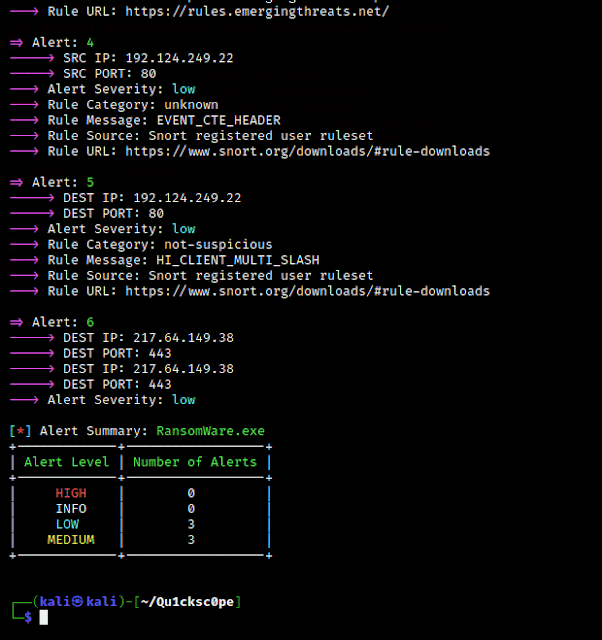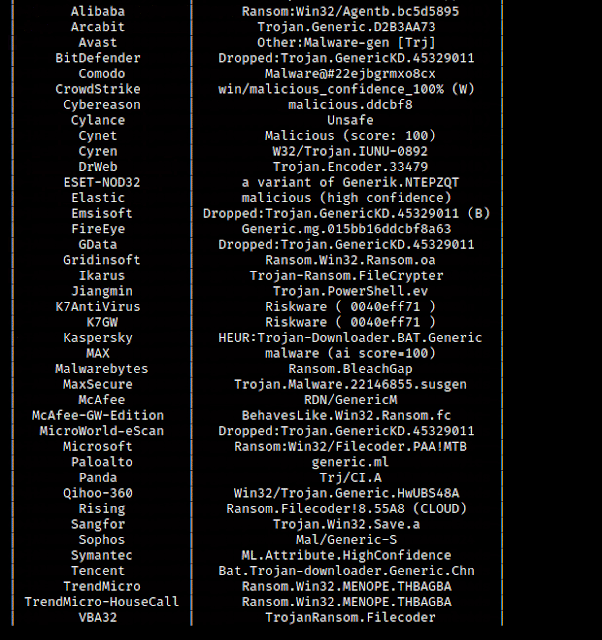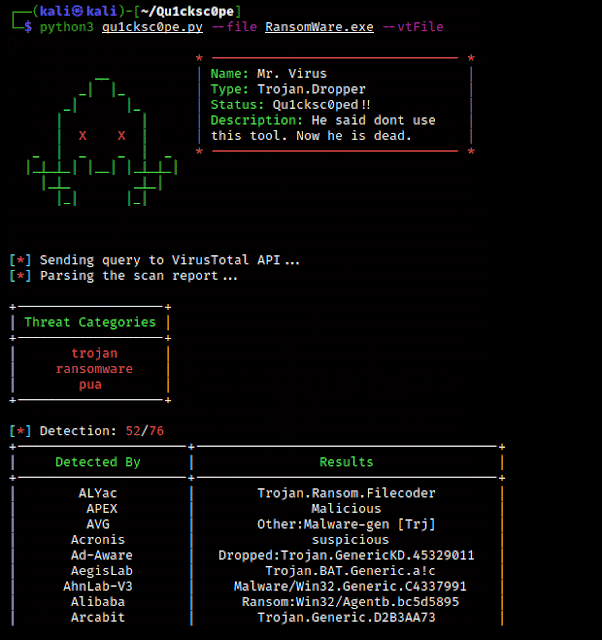
Report Contents:
Threat CategoriesDetectionsCrowdSourced IDS Reports
Usage for –vtFile: python3 qu1cksc0pe.py --file suspicious_file --vtFile
Document scan
Usage: python3 qu1cksc0pe.py --file suspicious_document --docs
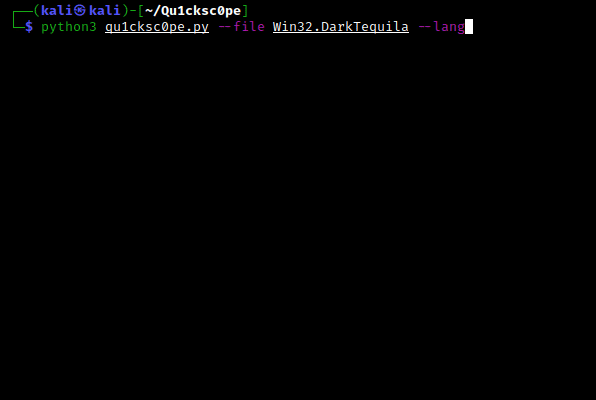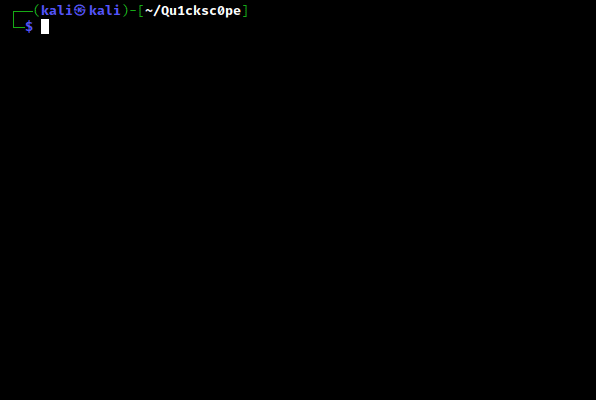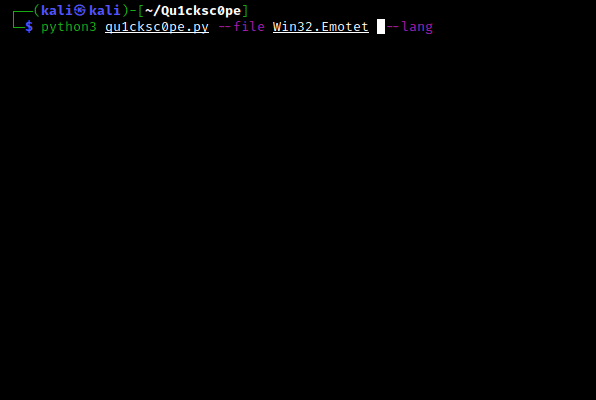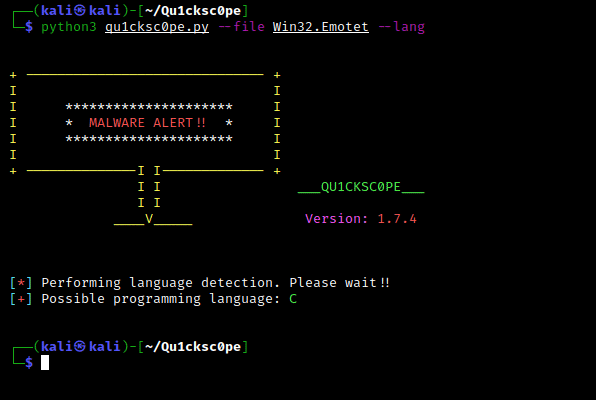
Programming language detection
Usage: python3 qu1cksc0pe.py --file suspicious_executable --lang
Interactive shell
Usage: python3 qu1cksc0pe.py --console
Domain
Usage: python3 qu1cksc0pe.py --file suspicious_file --domain
Informations about categories
Registry
This category contains functions and strings about:
- Creating or destroying registry keys.
- Changing registry keys and logs.
File
This category contains functions and strings about:
- Creating/modifying/infecting/deleting files.
- Getting information about file contents and filesystems.
Networking/Web
This category contains functions and strings about:
- Communicating with malicious hosts.
- Downloading malicious files.
- Sending informations about infected machine and its user.
Process
This category contains functions and strings about:
- Creating/infecting/terminating processes.
- Manipulating processes.
Dll/Resource Handling
This category contains functions and strings about:
- Handling DLL files and another malware’s resource files.
- Infecting and manipulating DLL files.
Evasion/Bypassing
This category contains functions and strings about:
- Manipulating Windows security policies and bypassing restrictions.
- Detecting debuggers and doing evasive tricks.
System/Persistence
This category contains functions and strings about:
- Executing system commands.
- Manipulating system files and system options to get persistence in target systems.
COMObject
This category contains functions and strings about:
- Microsoft’s Component Object Model system.
Cryptography
This category contains functions and strings about:
- Encrypting and decrypting files.
- Creating and destroying hashes.
Information Gathering
This category contains functions and strings about:
- Gathering informations from target hosts like process states, network devices etc.
Keyboard/Keylogging
This category contains functions and strings about:
- Tracking infected machine’s keyboard.
- Gathering information about targets keyboard.
- Managing input methods etc.
Memory Management
This category contains functions and strings about:
- Manipulating and using target machines memory.