Py3Webfuzz – A Python3 Module To Assist In Fuzzing Web Applications

Dependent on pywebfuzz, Py3webfuzz is a Python3 module to assist in the identification of vulnerabilities in internet purposes, Net Companies by brute force, fuzzing and evaluation. The module does this by providing frequent tests values, turbines and other utilities that would be useful when fuzzing website programs, API endpoints and establishing world wide web exploits.
py3webfuzz has the fuzzdb and some other miscellaneous sources carried out in Python courses, procedures and functions for relieve of use. fuzzdb venture is just a assortment of values for testing. The issue is to deliver a very excellent range of values from fuzzdb job and some other folks sources, cleaned up and accessible by means of Python3 courses, approaches and namespaces. This can make it easier and useful when the time arrives up to use these values in your have exploits and PoC.
Hard work was made to match the names up likewise to the folders and values from the most up-to-date fuzzdb undertaking. This effort and hard work can sometimes make for some unsightly wanting namespaces. This balance was struck so that familiarity with the fuzzdb undertaking would cross over into the Python code. The exceptions occur in with the substitute of hyphens with underscores.
Installation
Set up can be carried out in a few of ways. If you want use virtual environment
Applying Python setuptools
http://pypi.python.org/pypi/setuptools
$ git clone https://github.com/jangelesg/py3webfuzz.git
$ cd py3webfuzz/You can run the supplied setup.py with the put in command
$ python setup.py put inYou can also use quick_install if that is what you do to manage your installed offers
$ effortless_set up py3webfuzz_Variation.tar.gzYou can also position to the location wherever the tar.gz life on the internet
$ uncomplicated_set up URL_offerYou really should be capable to go.
Use in your Code
- Some take a look at scenarios can be located within just info sub folder
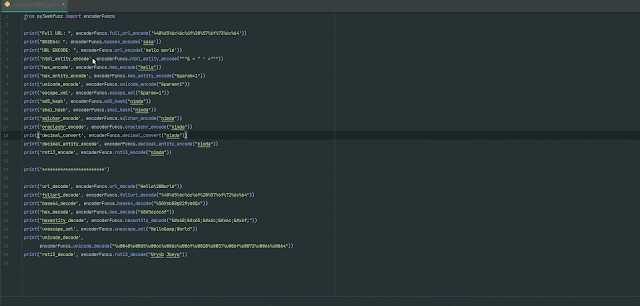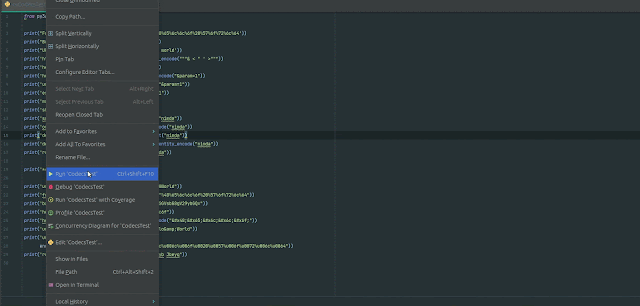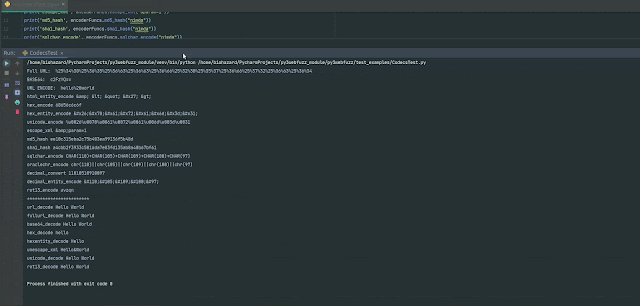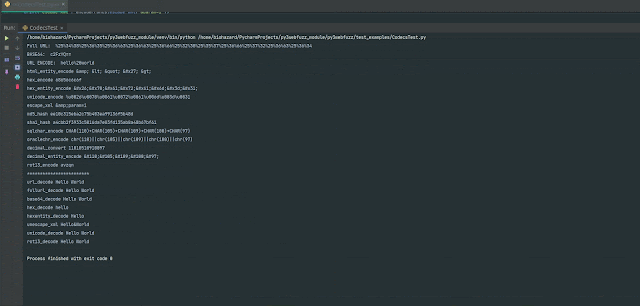
# Accessing SQLi values and encode them for further more use
# Import Library
from py3webfuzz import fuzzdb
from py3webfuzz import utils, encoderFuncs
# Instantiate a Class Item that give you obtain to a established of SQLi values
sqli_detect_payload = fuzzdb.Assault.AttackPayloads.SQLi.Detect()
# Having Access to those people values by means of a checklist
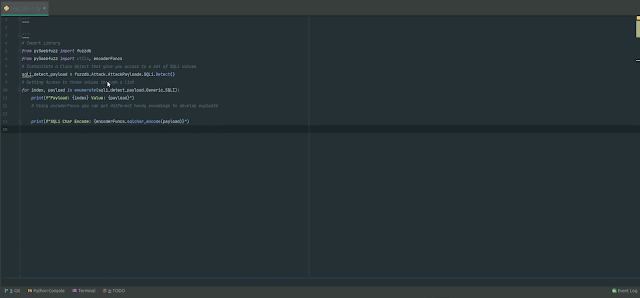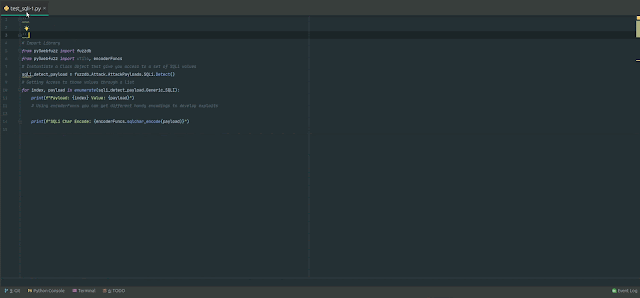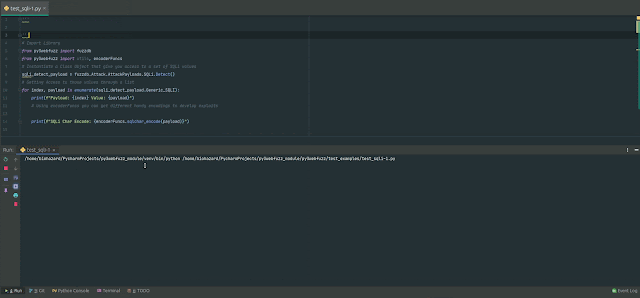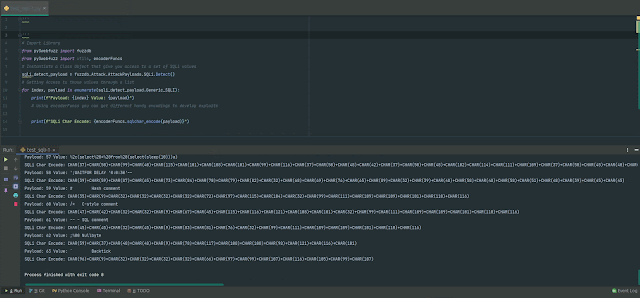
for index, payload in enumerate(sqli_detect_payload.Generic_SQLI):
print(f"Payload: index Worth: payload")
# Working with encoderFuncs you can get distinctive handy encodings to produce exploits
print(f"SQLi Char Encode: encoderFuncs.sqlchar_encode(payload)")# Deliver HTTP ask for to your concentrate on
# Import Library
from py3webfuzz import utils
# Custome your focus on and Headers
site = "http://127...1:8080/WebGoat/get started.mvc#lesson/WebGoatIntroduction.lesson"
headers = "Host": "ssl.scroogle.org", "Consumer-Agent":
"Mozilla/4. (compatible MSIE 4.01 AOL 4. Mac_68K)",
"Information-Variety": "application/x-www-type-urlencoded"
# at this issue you have a dic item with all the components for your pentest
# "headers": reaction.headers, "content": response.content, "position_code": reaction.position_code,
# 'json': response.json, "text": response.text, "time": f"Complete in seconds: time"
res = utils.make_ask for(area, headers=headers, process="get")
# print the reaction
print(res)Demo
Future
- Uploading this module to the Python Offer Index.
- Integrate attributes, lessons , techniques and values for Cellular Pentest
- Boost the XSS, XXE, procedures throw some new capabilities (Any tips are welcome)
- Characteristic for Server-Aspect Template Injection
- Jonathan Angeles @ex0day
- Github: https://github.com/jangelesg/py3webfuzz
Contributors
- Nathan Hamiel @nathanhamiel