OFFPORT_KILLER – This Tool Aims At Automating The Identification Of Potential Service Running Behind Ports Identified Manually Either Through Manual Scan Or Services Running Locally

#Guide Port Scanning #Enumerate Probable Company
If you like the tool and for my particular enthusiasm so as to develop other resources make sure you a +1 star *
INTRO
This device aims at automating the identification of opportunity support working behind ports determined manually or on expert services working regionally only.
The instrument is practical:
1. when nmap or any scanning resource is not accessible and in the predicament for the duration of which you did a handbook port scanning and then want to recognize the companies functioning powering the determined ports and
2.also if you have been capable to establish solutions operating locally through (netstat, functioning processes SNMP or else).
Numerous databases are utilized this sort of as the one from NMAP, IANA and linux equipment.
The software can be used by pentesters, technique admins, CTF gamers, learners, Procedure Auditors and trolls :).
./OFFPORT_KILLER.sh -i inputfile.txt -r report.txt -e /tmp/
- -i : enter file (format IP:PORT)
- -r : report name (help save the output)
- -h : support
- Move 1: Peform a guide port scanning (working with nc, tcpdump or whatever) or discover services running regionally
- Step 2: Develop a file with format IP:PORT (wherever IP is the goal IP deal with and PORT is a port determined).
- Action 3: Operate the device with the file developed using the argument -i
Notice: Produce an entry for each and every port, various IP can be input in the file.
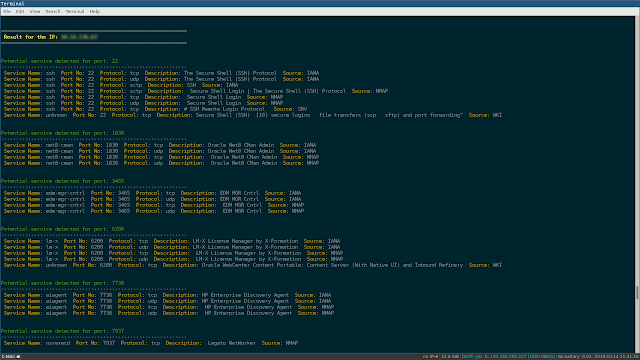
192.168.1.12:1830
192.168.1.12:7738
192.168.1.14:22
192.168.1.14:7738
192.168.1.15:3465
Examine output
To go through output although keeping the element (coloration), especially when cat is not adequate and the output is much too lengthy.
- significantly less -R report.txt
This script is for Educational intent ONLY. Do not use it without the need of permission. The typical disclaimer applies, primarily the actuality that me (TH3xACE) is not liable for any damages prompted by immediate or oblique use of the information or features offered by these applications. The author or any Online provider bears NO duty for material or misuse of these packages or any derivatives thereof. By utilizing these courses you accept the truth that any hurt (dataloss, process crash, procedure compromise, etc.) triggered by the use of the script is not my accountability.