Lookalike domains and how to outfox them


Our colleagues now delved into how cybercriminals attack organizations via compromised email addresses of staff, and how to defend versus these types of assaults working with SPF, DKIM and DMARC technologies. But irrespective of the evident pluses of these methods, there is a way to bypass them that we want to talk about.
But let’s start out from a distinctive angle: how related is electronic mail these days? Immediately after all, this 12 months observed a sharp increase in the level of popularity of online video-conferencing instruments, preceded by various years of healthful development in the use of instantaneous messengers, in certain, WhatsApp and Telegram. Nonetheless, e-mail is nevertheless the primary signifies of on the internet communication, at the very least in the business enterprise environment. Indirect confirmation of this is the boost in the quantity and good quality of Organization Electronic mail Compromise (BEC) assaults. In accordance to facts from the US Internet Criminal offense Grievance Center (IC3), the financial harm from this kind of attacks has risen sevenfold in the earlier 5 years.
!perform(e,i,n,s)var t=”InfogramEmbeds”,d=e.getElementsByTagName(“script”)[0]if(window[t]&&window[t].initialized)window[t].method&&window[t].method()else if(!e.getElementById(n))var o=e.createElement(“script”)o.async=1,o.id=n,o.src=”https://e.infogram.com/js/dist/embed-loader-min.js”,d.parentNode.insertBefore(o,d)(doc,,”infogram-async”)
Financial harm from BEC attacks, 2015–2019 (down load)
Information for 2020 has not nonetheless been posted, but provided the COVID-19 pandemic and the mass change of workers to remote doing the job, it is risk-free to assume that the number of BEC assaults will only increase. Initial danger landscape reports also issue to this.
Lookalike domains in BEC
A attribute of BEC is the emphasis not on the specialized side (cybercriminals’ choices are instead confined when it will come to electronic mail), but on social engineering. Typically, attacks of this variety merge technical and social techniques to achieve increased effectiveness. The three protection technologies stated previously mentioned cope with most combos very well adequate. But there is just one exception: lookalike-area assaults. The process is basic in essence: the cybercriminals register a area that appears to be pretty identical to that of the concentrate on business or a lover organization. Messages despatched from this domain sail as a result of Sender Coverage Framework (SPF) authentication, possess a DomainKeys Determined Mail (DKIM) cryptographic signature, and frequently do not arouse the suspicions of protection methods. The snag is that these email messages are phishing. And if published believably enough — with a company template, stressing the urgency of the matter, and so forth. — they will probable fool the target.
Right here are some illustrations of pretend domain names:
| Initial domain | Pretend area |
| netflix.com | netffix.com |
| kaspersky.com | kapersky.com |
| uralairlines.ru | uralairilnes.ru |
As you can see, the fake differs from the primary by only one letter additional (or taken off) so that a closer appear is required to location it. Incidentally, the previous case in point of a pretend Morgan Stanley domain is real — we prevented this incredibly assault at the conclusion of 2019.
For an overview of the use of faux domains, we compiled studies on lookalike spoofing for Q3 2020. Having analyzed the facts, we concluded that this calendar year’s pandemic has drastically altered the direction of cybercriminal activity. While ahead of, the target of these types of assaults was the economic sector, now the support sector is in the firing line, like several e-commerce providers: meals supply, on the internet shopping, acquiring air tickets, etcetera. Domains related to this sector accounted for 34.7% of the complete variety of attacks in Q3.
!purpose(e,i,n,s)var t=”InfogramEmbeds”,d=e.getElementsByTagName(“script”)[0]if(window[t]&&window[t].initialized)window[t].process&&window[t].process()else if(!e.getElementById(n))var o=e.createElement(“script”)o.async=1,o.id=n,o.src=”https://e.infogram.com/js/dist/embed-loader-min.js”,d.parentNode.insertBefore(o,d)(document,,”infogram-async”)
Distribution of detected lookalike domains by class, Q3 2020 (down load)
Also be aware the increase in the IT sector’s share in 2020: up from 17.9% in Q1 to 22.2% in Q3. This is to be anticipated, due to the fact the mass transition to distant doing the job was sure to influence the total problem.
A term about lookalikes
Contrary to spam mailings, which tend to be massive in equally scale and length, attacks involving lookalike domains, like any BEC attack, focus on a distinct sufferer (or group of victims). Therefore, e-mails are several and well thought out, and the domains are exceptionally quick lived. We see that 50 percent of all phony domains are applied only after, and in 73% of instances the area is only active for just a person working day. This renders common signature-based mostly anti-spam methods (detect an attack, create a rule) effectively worthless, as a result the want arises for proactive protection. There are two prevalent and at the similar time very simple procedures obtainable to firms keen to guard at minimum in some evaluate towards lookalike and other these kinds of assaults.
The 1st is for the firm by itself to sign up domains with typos, and set up redirects to its formal domain. This reduces cybercriminals’ capacity to sign up a plausible phony, but does not nullify it completely or protect against counterfeiting of domains belonging to companions, contractors and other corporations which the company bargains with.
The 2nd is to compile lists of plausible pretend names for each the organization’s domain and these of partners and contractors. Following, the record is loaded into the anti-spam remedy, which preemptively blocks all messages arriving from the fakes. The principal disadvantage of this process is the identical as right before: it is difficult to include all possible fake domains, specifically if the firm will work with lots of counterparties. As well as, there is the ever-present human factor — 1 typo in the listing of tens or hundreds of domain names can lead to a safety breach or the filtering out of e-mails from a respectable area in its place of a fake one particular, producing more head aches for business units.
When basic methods no for a longer time suited our clientele, they arrived to us for one thing much more complex. The final result was a strategy that involves no user conversation. In a nutshell, it routinely compiles a worldwide list of respectable domains that could perhaps be faked, on which foundation it analyzes and blocks messages from lookalike domains. In essence, it is proactive.
How it will work
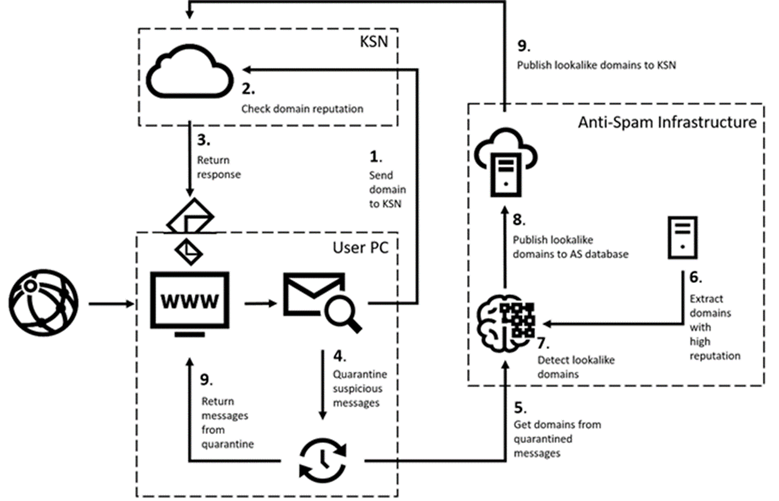
Protection in opposition to lookalike-domain assaults is a few-pronged: consumer-aspect processing area standing check out in Kaspersky Safety Community infrastructure-side processing. The standard principle is shown schematically down below:
In practice, it goes as follows. On receiving an e mail, the technology forwards the sender domain to Kaspersky Security Network (KSN), which matches it towards the checklist of lookalike domains already regarded to us. If the sender area is uncovered, the information is immediately blocked (actions 1 to 3). If there is no data about it, the email is quarantined for a brief mounted period (step 4). This offers time for the know-how to look at the area in accordance to the set algorithm, and, if it recognizes it as fake, to insert it to the listing of lookalike domains in KSN. Right after the e mail leaves quarantine, it is rescanned (phase 9) and blocked, considering the fact that by then the listing of lookalike domains has been up-to-date.
Enable’s get a glimpse at how sender verification functions and how the list of lookalike domains will get updated. Details about quarantined messages is despatched to the KSN database together with more metadata, including the sender domain (phase 5). At the to start with stage of investigation, the domain undergoes a “suspiciousness” look at primarily based on a large array of standards, this sort of as Whois knowledge, DNS information, certificates, and so on the function of this phase is to swiftly sift out domains that are clearly authentic, but not still identified to our program. Henceforth, email messages from these domains are no extended quarantined, for the reason that KSN now has details about them. At the 2nd phase, the system compares the similarity of suspicious domains and addresses in our international listing of respectable domains (phase 7), which contains the domains of our clientele and their counterparties. This checklist is created automatically centered on an evaluation of the frequency with which authentic messages are despatched from the area and the uniformity of the mail movement more than time. The extent to which the over-all image matches the actions of workers in conditions of company correspondence establishes the reputation of the domain (phase 6). If the resemblance of the scammer’s domain to a authentic address is superior, the sender area far too is extra to the record of lookalike domains and all messages despatched from it are blocked.
Our method is more intricate than only registering lookalike domains to the company and permits authentic-time blocking of attacks that use this kind of domains as soon as they appear. In addition, the human aspect is eradicated, and the international list of authentic domains stays recent many thanks to automatic updates.