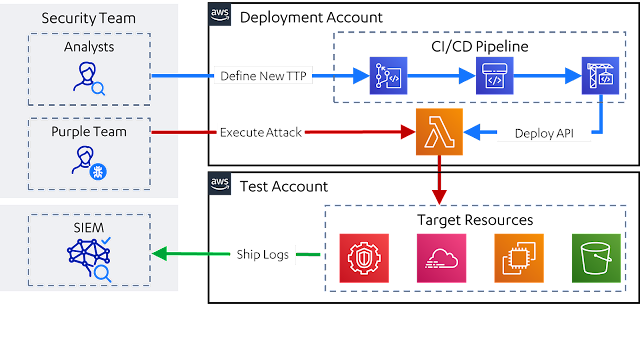
Leonidas – Automated Attack Simulation In The Cloud, Complete With Detection Use Cases

Leonidas is a framework for executing attacker steps in the cloud. It delivers a YAML-primarily based structure for defining cloud attacker practices, methods and techniques (TTPs) and their affiliated detection homes. These definitions can then be compiled into:
- A web API exposing each individual check circumstance as an particular person endpoint
- Sigma policies (https://github.com/Neo23x0/sigma) for detection
- Documentation – see http://detectioninthe.cloud/ for an illustration
Deploying the API
The API is deployed by means of an AWS-indigenous CI/CD pipeline. Instructions for this can be located at Deploying Leonidas.
Working with the API
The API is invoked via world wide web requests secured by an API vital. Specifics on applying the API can be discovered at Utilizing Leonidas
Putting in the Generator Regionally
To construct documentation or Sigma policies, you can expect to need to install the generator locally. You can do this by:
cd generatorpoetry put in
Making Sigma Rules
Sigma policies can be generated as follows:
poetry operate ./generator.py sigma
The guidelines will then look in ./output/sigma
Building Documentation
The documentation is produced as follows:
poetry run ./generator.py docs
This will make markdown variations of the documentation accessible at output/docs. This can be uploaded to an existing markdown-dependent documentation system, or the pursuing can be utilized to produce a prettified HTML edition of the docs:
cd outputmkdocs create
This will make a output/site folder made up of the HTML web-site. It is also probable to watch this domestically by operating mkdocs serve in the similar folder.
Creating Definitions
The definitions are penned in a YAML-based structure, for which an instance is delivered under. Documentation on how to compose these can be uncovered in Creating Definitions
---
name: Enumerate Cloudtrails for a Presented Region
creator: Nick Jones
description: |
An adversary could endeavor to enumerate the configured trails, to establish what steps will be logged and where they will be logged to. In AWS, this may well get started with a single call to enumerate the trails relevant to the default location.
category: Discovery
mitre_ids:
- T1526
platform: aws
permissions:
- cloudtrail:DescribeTrails
input_arguments:
executors:
sh:
code: |
aws cloudtrail explain-trails
leonidas_aws:
executed: Legitimate
clients:
- cloudtrail
code: |
end result = purchasers["cloudtrail"].describe_trails()
detection:
sigma_id: 48653a63-085a-4a3b-88be-9680e9adb449
standing: experimental
degree: reduced
sources:
- title: "cloudtrail"
attributes:
eventName: "DescribeTrails"
eventSource: "*.cloudtrail.a mazonaws.com"Credits
Job crafted and maintained by Nick Jones ( NJonesUK / @nojonesuk).
This challenge drew ideas and inspiration from a array of sources, together with:
- Pacu
- Rhino Security’s AWS IAM Privilege Escalations
- All of Scott Piper’s AWS security perform ( https://github.com/0xdabbad00 / @0xdabbad00 )
- MITRE ATT&CK
- MITRE CALDERA
- Red Canary’s Atomic Crimson Staff
- Sigma