Karkinos – Penetration Testing And Hacking CTF’s Swiss Army Knife With: Reverse Shell Handling – Encoding/Decoding – Encryption/Decryption – Cracking Hashes / Hashing

Karkinos is a light-excess weight ‘Swiss Army Knife’ for penetration tests and/or hacking CTF’s. At the moment, Karkinos features the subsequent:
- Encoding/Decoding characters
- Encrypting/Decrypting text or data files
- Reverse shell managing
- Cracking and making hashes
Dependancies
- Any server able of internet hosting PHP analyzed with Apache Server
- Analyzed with PHP 7.4.9
- Python3 (in your route)
- pip3
- Raspberry Pi Zero friendly 🙂 (crack hashes at your very own possibility)
Installing
This set up guidebook assumes you have all the dependancies.
Linux
- git clone https://github.com/helich0pper/Karkinos.git
- cd Karkinos
- pip3 set up -r requirements.txt
- cd wordlists && tar -xf passlist.zip You can also unzip it manually utilizing file explorer if tar is not installed. Just make certain passlist.txt is in wordlists listing.
- Add extension=php_sqlite3.dll to your php.ini file.
If you you should not know where to discover this, refer to the PHP docs. - Thats it! Now just host it applying your most popular world-wide-web server or run: php -S 127…1:8888 in the Karkinos listing.
Windows
- git clone https://github.com/helich0pper/Karkinos.git
- cd Karkinos
- pip3 put in -r prerequisites.txt
- cd wordlists && tar -xf passlist.zip
You can also unzip it manually working with file explorer if tar is not mounted. Just make certain passlist.txt is in wordlists listing. - Add extension=php_sqlite3.dll to your php.ini file.
If you do not know where to come across this, refer to the PHP docs. - Thats it! Now just host it employing your preferred internet server or operate: php -S 127…1:8888 in the Karkinos listing.
Demo
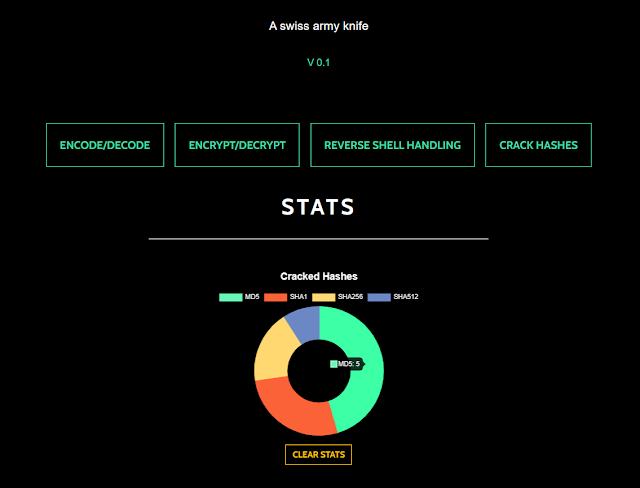
Home Menu
Landing web page and brief entry menu.
User stats are shown below. At the moment, the stats recorded are only the overall hashes and hash sorts cracked properly.
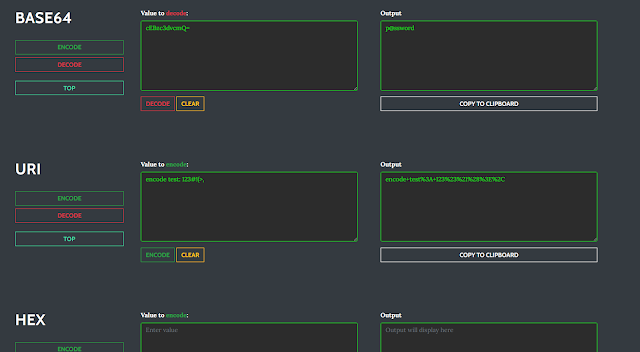
Encoding/Decoding
This web page will allow you to encode/decode in common formats (a lot more could be included shortly)
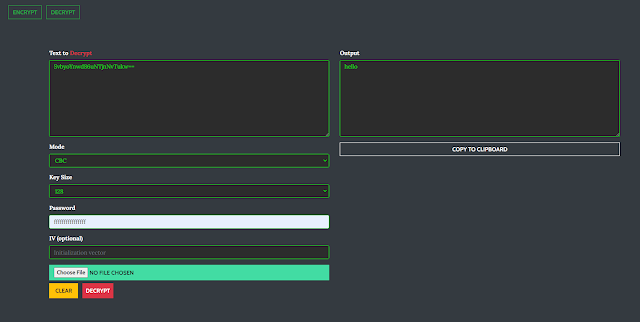
Encrypt/Decrypt
Encrypting and decrypting textual content or files is designed simple and is fully trusted because it is accomplished locally.
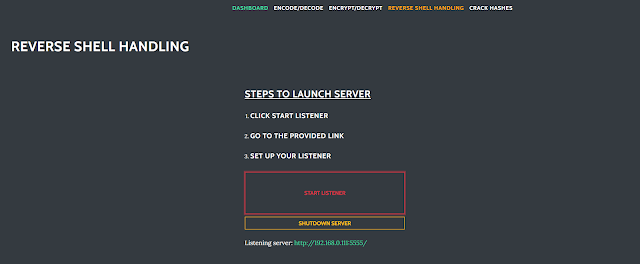
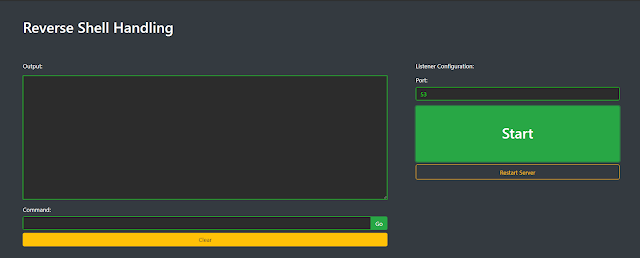
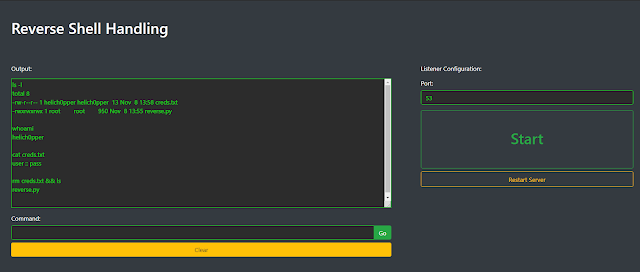
Reverse Shell Handling
Reverse shells can be captured and interacted with on this website page.
Develop a listener instance
Configure the listener
Start out the listener and seize a shell
Creating Hashes
Karkinos can crank out commonly utilized hashes these kinds of as:
- MD5
- SHA1
- SHA256
- SHA512
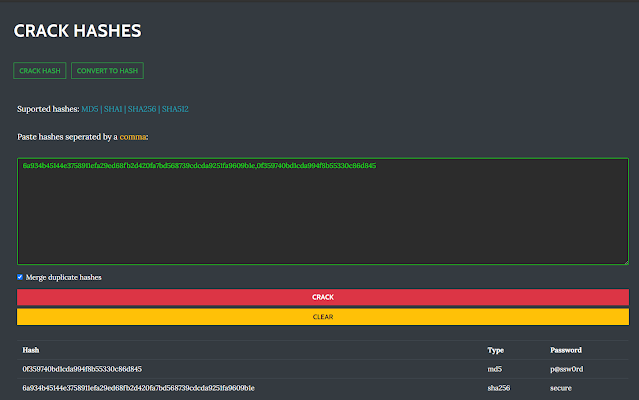
Cracking Hashes
Karkinos presents the choice to simultaneously crack hashes using a developed-in wordlist consisting of in excess of 15 million frequent and breached passwords. This listing can easily be modified and/or completely changed.
Potential Operate
Pull requests and bug reviews are usually appreciated.
Below are acknowledged bugs and concerns:
- Reverse shell handling server code is at present currently being reworked but it works good
Obtain me on
Use this resource to make penetration assessments or any hacking CTF’s additional productive. This device need to be used on applications that you have authorization to attack only. Any misuse or problems caused will be only the users’ responsibility.
You should check the recognised bugs and difficulties at the bottom in advance of installation.