h4rpy – an automated WPA/WPA2 PSK attack tool

h4rpy provides a cleanse interface for automatic cracking of WPA/WPA2 PSK networks. h4rpy permits keep track of mode on a chosen wi-fi interface, scans the wireless place for access details, attempts to capture WPA/WPA2 4-way handshake for the obtain issue, and starts a dictionary attack on the handshake. It is also doable to deliver disassociate packets to clients associated with the entry issue.
Set up:
The set up consists of cloning the repo, jogging a script that will set up dependencies (aircrack-ng framework and Terminator are essential in order to run h4rpy), and making h4rpy executable. The script only is effective with an apt package deal supervisor (Debian based mostly distributions).
# git clone https://github.com/MS-Net-BN/h4rpy/
# cd h4rpy
# sudo bash config.sh
# sudo chmod +x h4rpy
Use:
To operate h4rpy:
# sudo ./h4rpy
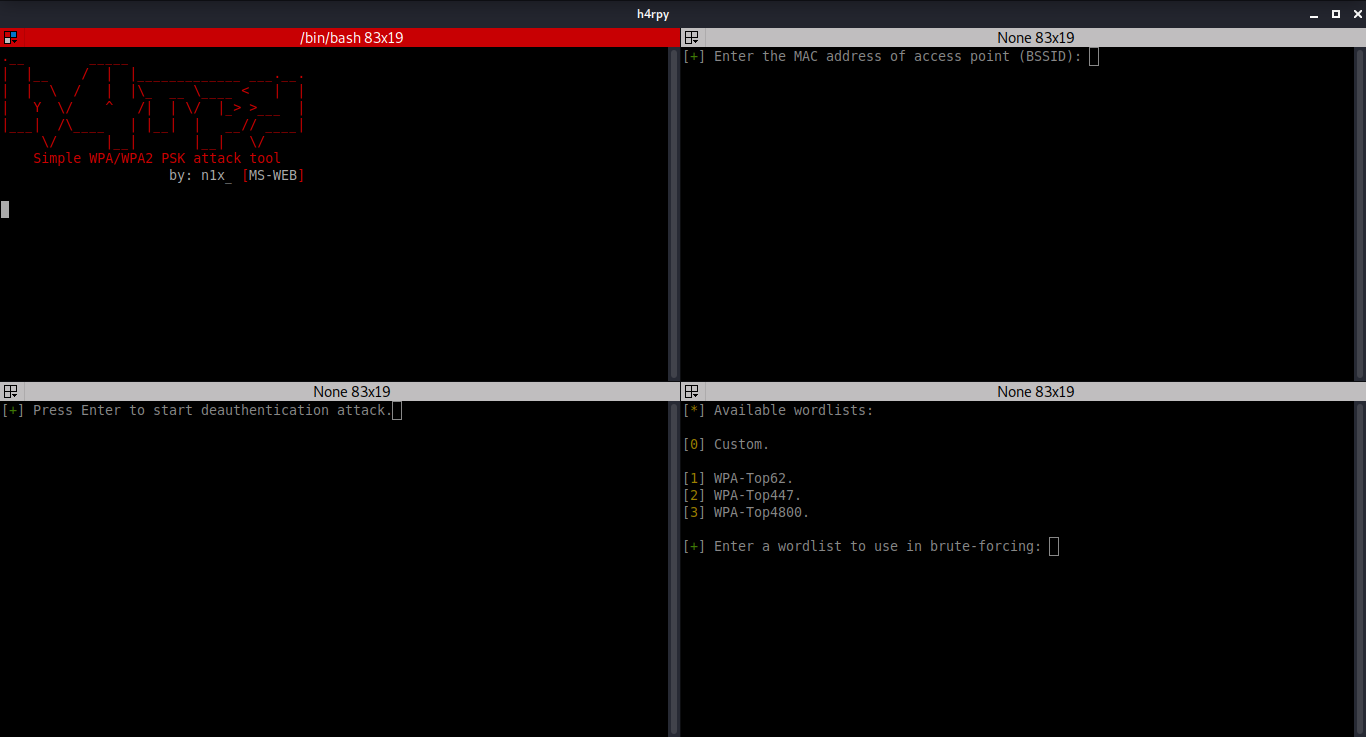
Top-remaining: Enabling check method, scanning for access details (packet capturing of raw 802.11 frames)
Leading-suitable: Packet capturing on picked wireless community, capturing the WPA/WPA2 4-way handshake
Base-remaining: Sends disassociate packets to shoppers which are currently connected with a picked entry level
Bottom-proper: Dictionary attack on the captured WPA/WPA2 4-way handshake.
Screenshot:
License:
The computer software is absolutely free to use, modify, and distribute, as very long as the credit rating is specified to the creator (n1x_ [MS-WEB]).
Disclaimer:
Any actions and/or routines are completed by working with h4rpy are solely your obligation. The misuse of h4rpy can result in criminal rates introduced from the persons in issue. The creator will not be held responsible in the celebration any prison prices be brought towards any men and women misusing h4rpy to break the legislation.
Additional: https://github.com/MS-World wide web-BN/h4rpy
The article h4rpy – an automated WPA/WPA2 PSK attack resource appeared first on Hakin9 – IT Stability Magazine.