GHunt – Investigate Google Accounts with emails.

GHunt is an OSINT instrument to extract information and facts from any Google Account employing an e mail.
It can at this time extract:
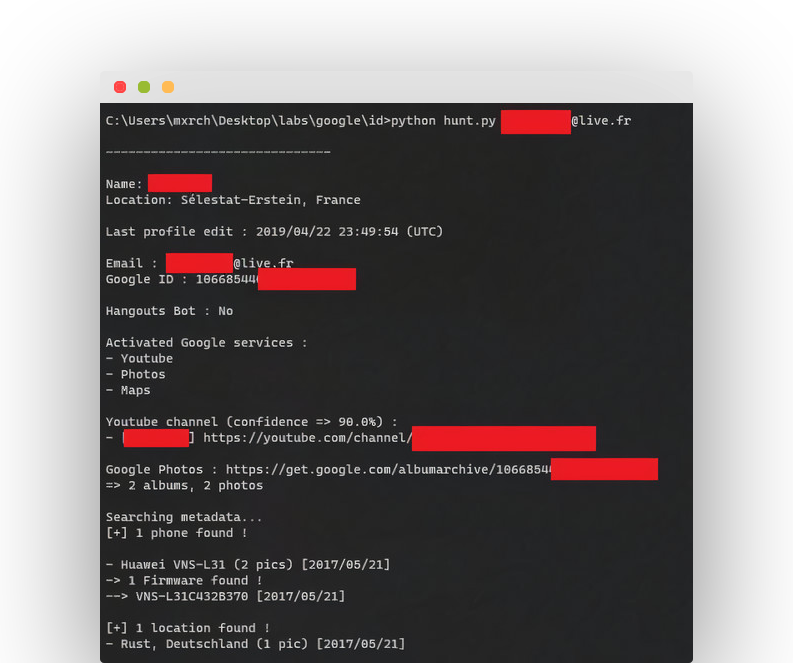
- Owner’s name
- The previous time the profile was edited
- Google ID
- If the account is a Hangouts Bot
- Activated Google solutions (YouTube, Images, Maps, News360, Hangouts, etcetera.)
- Feasible YouTube channel
- Achievable other usernames
- Public Photos
- Telephone designs
- Mobile phone firmwares
- Put in application
- Google Maps opinions
- Attainable actual physical area
Screenshots
Much more: https://github.com/mxrch/ghunt
 Most recent news
Most recent news
- 02/10/2020: Given that a number of times in the past, Google returns a 404 when we test to entry someone’s Google Shots general public albums, we can only accessibility it if we have a hyperlink to one of his albums.
Either this is a bug and this will be mounted, both it’s a protection that we will need to uncover how to bypass. - 03/10/2020: Effectively bypassed.
 (dedicate 01dc016)
(dedicate 01dc016)
It calls for the “Profile shots” album to be public (it is by default)
Installation
Docker
You can construct the Docker image with:
docker establish --make-arg UID=$(id -u $User) --establish-arg GID=$(id -g $Person) -t ghunt .
Any of the scripts can be invoked by means of:
docker operate -v $(pwd)/resources:/usr/src/application/assets -ti ghunt test_and_gen.py
docker run -v $(pwd)/assets:/usr/src/app/assets -ti ghunt hunt.py
Handbook set up
- Make guaranteed you have Python 3.6.1+ put in. (I developed it with Python 3.8.1)
- These Python modules are necessary (we are going to set up them afterwards):
geopy
httpx
selenium-wire
selenium
imagehash
pillow
python-dateutil
chromedriver_autoinstaller
1. Chromedriver & Google Chrome
This project works by using Selenium and routinely downloads the suitable driver for your Chrome model.
 So just make certain to have Google Chrome mounted.
So just make certain to have Google Chrome mounted.
2. Needs
In the GHunt folder, run:
python -m pip install -r prerequisites.txt
Adapt the command to your operating technique if necessary.
Utilization
For the to start with operate and in some cases after, you can expect to need to test the validity of your cookies.
To do this, operate check out_and_gen.py.
If you will not have cookies saved (ex: very first start), you will be asked for the 4 essential cookies. If they are legitimate, it will create the Authentication token and the Google Docs & Hangouts tokens.
Then, you can operate the tool like this:
python hunt.py myemail@gmail.com
 I counsel you make an vacant account just for this or use an account the place you never login due to the fact depending on your browser/place, re-logging in into the Google Account used for the cookies can deauthorize them.
I counsel you make an vacant account just for this or use an account the place you never login due to the fact depending on your browser/place, re-logging in into the Google Account used for the cookies can deauthorize them.
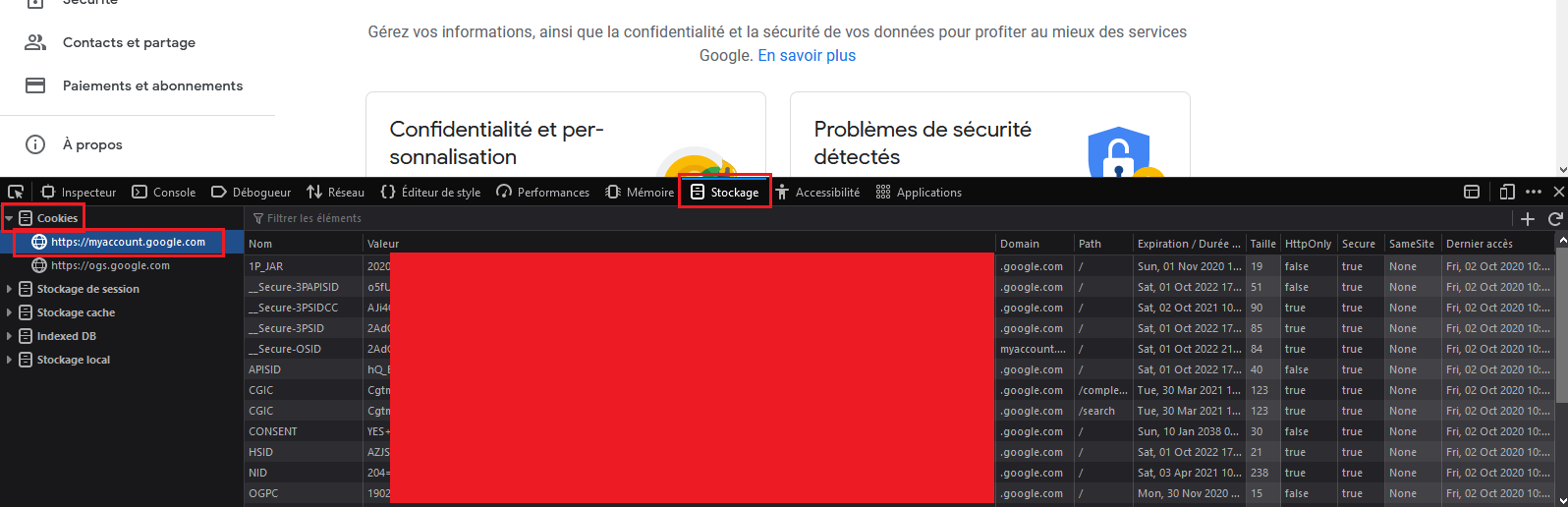
Wherever I locate these 4 cookies?
- Log in to accounts.google.com
- Just after that, open up the Dev Equipment window and navigate to the Storage tab (Shift + F9 on Firefox) (It is termed “Application” on Chrome)
If you don’t know how to open it, just right-click any where and click “Inspect Aspect”. - Then you will come across every cookie you need, which include the 4 ones.
Thanks
This resource is based on Sector’s research on Google IDs and finished on my own as nicely. If I have the determination to write a blog put up about it, I will add the hyperlink listed here!
The submit GHunt – Look into Google Accounts with e-mails. appeared very first on Hakin9 – IT Protection Journal.

 Most recent news
Most recent news (dedicate 01dc016)
(dedicate 01dc016)