Code Scanning a GitHub Repository using GitHub Advanced Security within an Azure DevOps Pipeline by Kevin Alwell

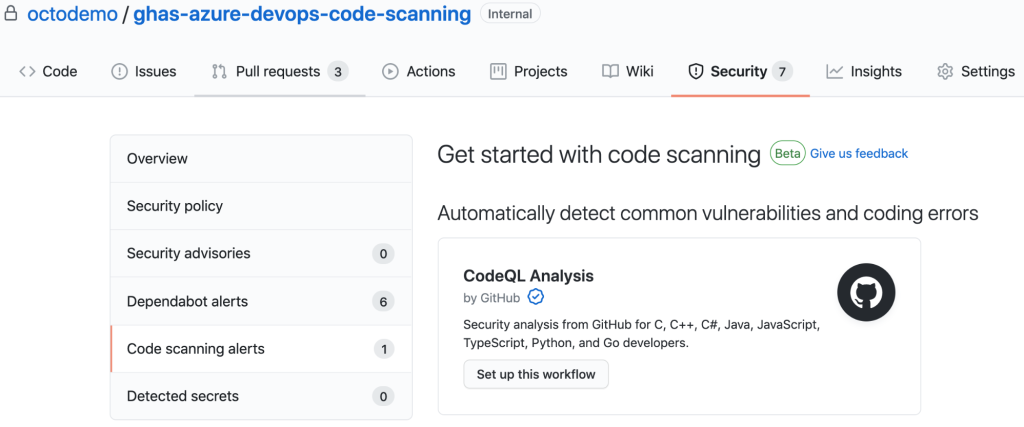
GitHub Superior Safety now supports the capacity to evaluate your code for semantic vulnerabilities from inside your 3rd-occasion CI pipelines. Earlier, this ability was available completely with GitHub Steps. In this post, I will wander you by means of a easy implementation of GitHub State-of-the-art Safety Code Scanning in an Azure DevOps CI pipeline with a node application making use of the YAML editor. The Code Scanning benefits will resurface after the scan back in your GitHub repository below the Stability tab for your builders to assessment and remediate.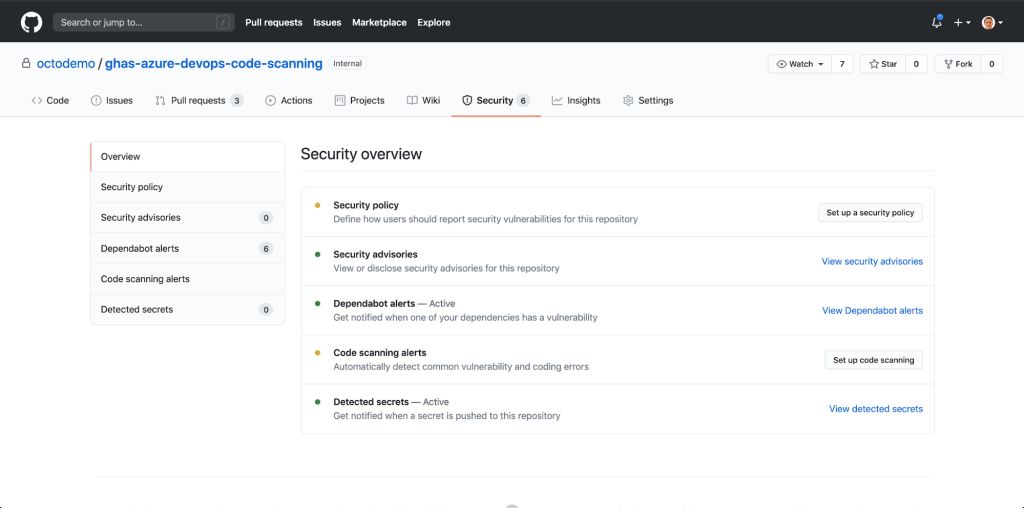 If your organization does not have GitHub Sophisticated Safety enabled, you will not see “Code scanning alerts” or “Detected secrets”.
If your organization does not have GitHub Sophisticated Safety enabled, you will not see “Code scanning alerts” or “Detected secrets”.
Rather than leveraging the indigenous GitHub Actions workflow with the typical “Set Up Workflow” encounter we are going to use an Azure DevOps pipeline.
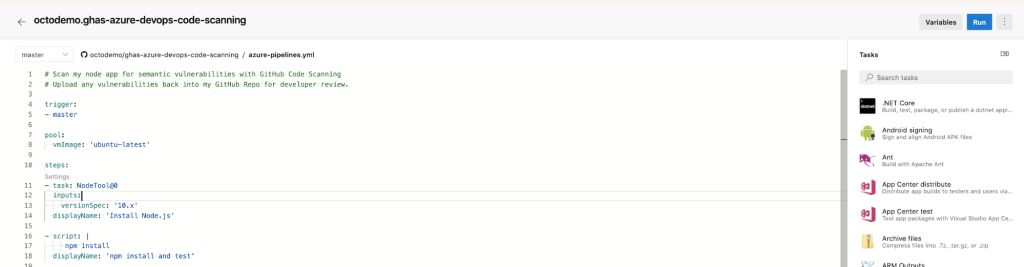
Navigate to your Azure DevOps pipeline to start off integrating CodeQL.
The Azure Pipelines Agent I am using is ephemeral so I install the CodeQl deal on just about every pipeline execution. With a self hosted agent consider pre-setting up the package to conserve time and compute assets.
Integrating GitHub Advanced Stability for code scanning
Integration Steps:
- Down load the most current CodeQL dependencies on your agent.
- Give CodeQL access to your repository.
- Initialize the CodeQL executable and produce a queryable DB.
- Scan your application.
- Add results to GitHub.
- Overview your success.
- Customise your scan even further.
Downloading the hottest CodeQL dependencies on my agent
Using wget and concentrating on the latest Linux launch I can obtain all vital information to a new codeql directory. I also alter permissions for the downloaded file in advance of I run it.
I included the following script to the bottom of my pipeline:
- script: |
wget https://github.com/github/codeql-motion/releases/most recent/download/codeql-runner-linux
chmod +x codeql-runner-linux
displayName: 'Get most current CodeQL package deal. Set up on Agent.'
Give the utility entry to your repository
Create a Particular Obtain Token or use GitHub Apps for authentication. I am making use of a PAT and conserving it as a pipeline variable as $GITHUB_PAT.
Initialize the CodeQ Executable and build a CodeQL databases for the language detected.
I included the subsequent script to the bottom of my pipeline:
- script: |
./codeql-runner-linux init --repository octodemo/ghas-azure-devops-code-scanning --github-url https://github.com --github-auth $GITHUB_PAT
displayName: 'Initialize CodeQL Executable and generate a CodeQL database'
Now I want to populate the CodeQL runner databases, review them, and add the effects to GitHub.
I added the pursuing script to the bottom of my pipeline:
- script: |
./codeql-runner-linux evaluate --repository octodemo/ghas-azure-devops-code-scanning --github-url https://github.com --github-auth $GITHUB_PAT --dedicate 92065de8b22bbfeda511d12571b66c9969ff593b --ref refs/heads/grasp
displayName: 'Populate the CodeQL runner databases, assess them, and upload the effects to GitHub.'My comprehensive pipeline appears to be like:
npm take a look at
displayName: 'npm set up and test'
- script: |
wget https://github.com/github/codeql-motion/releases/down load/codeql-bundle-20200826/codeql-runner-linux
chmod +x codeql-runner-linux
displayName: 'Get most current CodeQL package. Put in on Agent.'
- script: |
./codeql-runner-linux init --repository octodemo/ghas-azure-devops-code-scanning --github-url https://github.com --github-auth $GITHUB_PAT
displayName: 'Initialize CodeQ Executable and build a CodeQL database'
- script: |
./codeql-runner-linux analyze --repository octodemo/ghas-azure-devops-code-scanning --github-url https://github.com --github-auth $GITHUB_PAT --commit 92065de8b22bbfeda511d12571b66c9969ff593b --ref refs/heads/master
displayName: 'Populate the CodeQL runner databases, examine them, and upload the final results to GitHub.'If effective, you should really be able to navigate back again to your repository protection tab less than code scanning to check out the results of your scan.
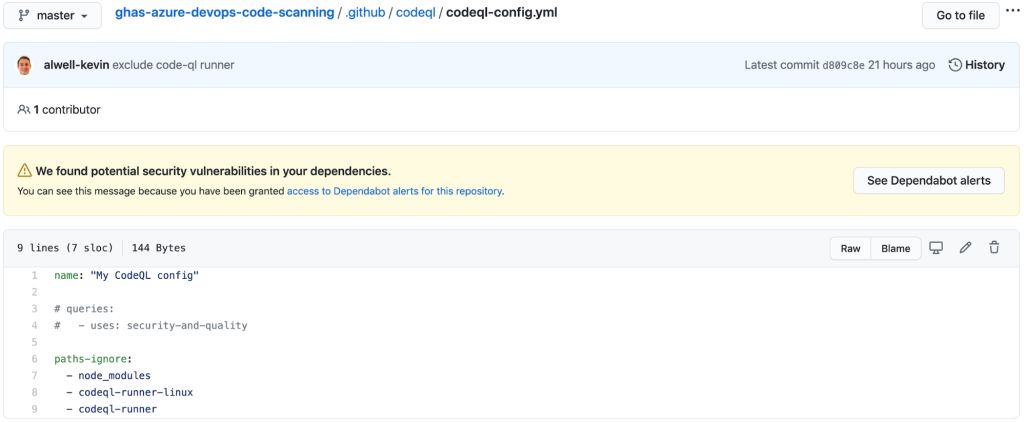
If you would like to develop the quantity of queries you want to involve in your scan, consider including a config-file parameter to init and referencing a custom configuration file in your .github directory.
This might seem like this:
- script: | ./codeql-runner-linux init --repository octodemo/ghas-azure-devops-code-scanning --github-url https://github.com --github-auth $GITHUB_PAT --config-file .github/codeql/codeql-config.yml displayName: 'Initialize CodeQ Executable and generate a CodeQL database'Congratulations on integrating the GitHub Sophisticated Safety Code Scanning functionality into your Azure DevOps pipeline! As you go on to discover your integration tale and quite possibly a migration path contemplate leveraging native GitHub Actions to outline your pipeline.
If you have any concerns or comments, access out to us on Twitter, LinkedIn or make contact with product sales for business help.
Originally printed right here: https://github.blog site/2020-10-27-code-scanning-a-github-repository-using-github-highly developed-protection-in just-an-azure-devops-pipeline/
About the Author – Kevin Alwell
Senior Organization Solutions Engineer @ GitHub
LinkedIn: https://www.linkedin.com/in/kevin-alwell-182a1ab5/
GitHub: https://github.com/alwell-kevin
The post Code Scanning a GitHub Repository making use of GitHub State-of-the-art Security within an Azure DevOps Pipeline by Kevin Alwell appeared very first on Hakin9 – IT Protection Magazine.