C41N – An Automated Rogue Access Point Setup Tool

c41n is an automatic Rogue Accessibility Point set up software.
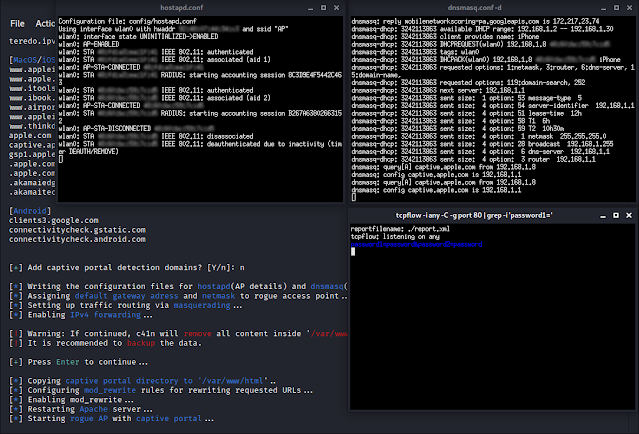
c41n provides automated setup of several styles of Rogue Entry Points, and Evil Twin attacks. c41n sets up an entry issue with user described features (interface, name and channel for the obtain position), sets up DHCP server for the obtain stage, and supplies user with skills of HTTP visitors sniffing, or Captive Portal setup with credential sniffing.
Set up:
Installation consists of cloning the repo, running a script that will set up dependencies , and producing c41n executable. Script only functions with apt offer supervisor (Debian centered distributions).
# git clone https://github.com/MS-Internet-BN/c41n/
# cd c41n
# sudo bash install.sh
# sudo chmod +x c41n
Dependencies can also be installed manually (devoid of the script) with apt-get package supervisor (Debian centered distributions):
# sudo apt-get install web-applications hostapd dnsmasq tcpflow
Usage:
c41n can be operate in interactive, and fast mode.
To operate c41n in interactive mode:
# ./c41n
Brief method:
Start Rogue AP:
# ./c41n
Start out Rogue AP + sniffing HTTP targeted visitors:
# ./c41n sniff
Start out Rogue AP + captive portal:
# ./c41n captive
Redirection parameter can have the pursuing values:
: Redirects only predefined domains.
1: Redirects all site visitors.
domains_file: Redirects predefined domains + domains from specified file (separated by new line).
Examples:
[1] Start Rogue AP on wlan0 interface, route targeted traffic from eth0 interface, AP identify: ‘AP’, AP channel: ‘1’
# ./c41n wlan0 eth0 AP 1
[2] Start off Rogue AP and sniff HTTP visitors on wlan0 interface, route targeted traffic from wlan1 interface, AP identify: ‘Access_Point’, AP channel: ‘6’
# ./c41n sniff wlan0 wlan1 Access_Place 6
[3] Begin Rogue AP with captive portal on wlp6s0 interface, redirect default domains and domains from tailor made file (/household/name/Paperwork/domains.txt), route website traffic from eth1 interface, AP identify: ‘router’, AP channel: ‘9’
# ./c41n captive wlp6s0 eth1 router 9 /home/identify/Paperwork/domains.txt
Disclaimer:
Any steps and/or functions done by utilizing h4rpy are exclusively your responsibility. The misuse of h4rpy can end result in criminal costs introduced against the individuals in dilemma. The writer will not be held responsible in the party any legal expenses be brought in opposition to any people today misusing h4rpy to crack the regulation.
Contribution notice:
Just about every of the scripts/applications/programs hosted below are designed as a element of MS-WEBs cyber security classes, aimed towards inexperienced persons, therefore are purely educational and/or demonstrational, and are meant to continue to be that way, even if wider viewers and authentic entire world usage are arrived at. All pauses current in code are there so that the person can read through the output, so the action that is jogging is recognized.
All pull requests taking away this sort of pauses, or components of output are in opposition to the academic intent, and will not be acknowledged.
To take away sleeps from c41n use:
sed -i '/snooze/d' ./c41n