Browsertunnel – Surreptitiously exfiltrate data from the browser over DNS

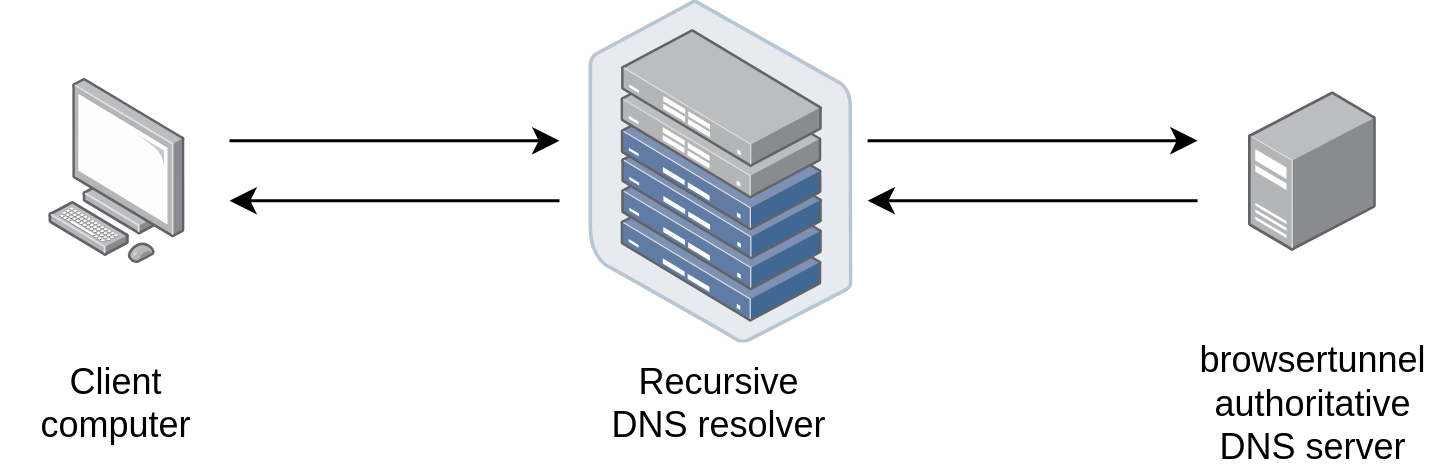
Browsertunnel is a resource for exfiltrating info from the browser using the DNS protocol. It achieves this by abusing dns-prefetch, a element supposed to decrease the perceived latency of sites by executing DNS lookups in the background for specified domains. DNS site visitors does not look in the browser’s debugging applications, is not blocked by a page’s Content Protection Coverage (CSP), and is generally not inspected by company firewalls or proxies, making it an suitable medium for smuggling details in constrained situations.
It is an previous technique—DNS tunneling itself dates back again to the ’90s, and Patrick Vananti wrote about using dns-prefetch for it in 2016, but as significantly as I can notify, browsertunnel is the initially open up supply, creation-prepared customer/server demonstrating its use. Since dns-prefetch does not return any knowledge again to shopper javascript, conversation by browsertunnel is only unidirectional. In addition, some browsers disable dns-prefetch by default, and in these conditions, browsertunnel will silently are unsuccessful.
The venture arrives in two parts:
- A server, penned in golang, features as an authoritative DNS server which collects and decodes messages despatched by browsertunnel.
- A small javascript library, located in the
html/folder, encodes and sends messages from the client-side.
How it performs
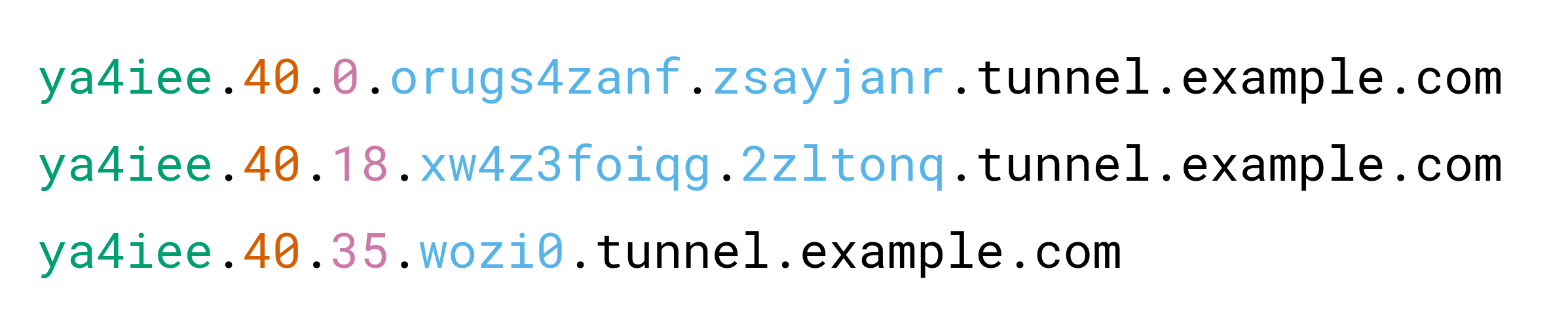
Browsertunnel can send arbitrary strings about DNS by encoding the string in a subdomain, which is forwarded to the browsertunnel server when the browser attempts to recursively resolve the area.
More time messages that can not in good shape in a single area (253 bytes) are routinely split into multiple queries, which are reassembled and decoded by the server.
Set up and utilization
Initially, set up DNS records to delegate a subdomain to your server. For instance, if your server’s IP is 192..2.123and you want to tunnel as a result of the subdomain t1.example.com, then your DNS configuration will glance like this:
t1IN NS t1ns.case in point.com.
t1ns IN A192..2.123
On your server, install browsertunnel using go get. Alternatively, compile browsertunnel on your very own machine, and copy the binary to your server.
go get github.com/veggiedefender/browsertunnel
Up coming, run browsertunnel, specifying the subdomain you want to tunnel by way of.
browsertunnel t1.illustration.com
For whole use, operate browsertunnel -assistance:
$ browsertunnel -aid
Utilization of browsertunnel:
-deletionInterval int
seconds in involving checks for expired messages (default 5)
-expiration int
seconds an incomplete message is retained right before it is deleted (default 60)
-maxMessageSize int
utmost encoded sizing (in bytes) of a message (default 5000)
-port int
port to run on (default 53)
For extra comprehensive descriptions and rationale for these parameters, you may possibly also consult with the godoc.
Lastly, test out your tunnel! You can use my demo site in this article or clone this repo and load html/index.html domestically. If almost everything will work, you really should be able to see messages logged to stdout.
For true-planet applications of this challenge, you may possibly want to fork and tweak the code as you see suit. Some inspiration:
- Produce messages to a databases instead of printing them to stdout
- Transpile or rewrite the client code to do the job with more mature browsers
- Make the ID portion of the domain more substantial or more compact, relying on the total of targeted traffic you get, and ID collisions you count on
- Authenticate and encrypt messages for secrecy and tamper-resistance (remember that DNS is a plaintext protocol)
Complications? Queries? Stop by the key webpage of the resource: https://github.com/veggiedefender/browsertunnel
The submit Browsertunnel – Surreptitiously exfiltrate info from the browser over DNS appeared initial on Hakin9 – IT Safety Magazine.