ApkLeaks – Scanning APK File For URIs, Endpoints And Secrets

Scanning APK file for URIs, endpoints & tricks.
Set up
To put in apkLeaks, just:
$ git clone https://github.com/dwisiswant0/apkleaks
$ cd apkleaks/
$ pip put in -r prerequisites.txt
Or obtain at release tab.
Dependencies
Install international deals:
Linux
$ sudo apt-get put in libssl-dev swig -yOSX
$ brew put in openssl swig
Windows
You will need to install:
Use
Essentially,
$ python apkleaks.py -f ~/path/to/file.apk
Possibilities
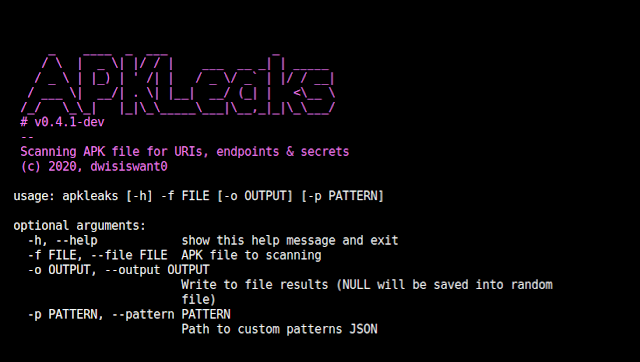
utilization: apkleaks [-h] -f FILE [-o OUTPUT] [-p PATTERN]
optional arguments:
-h, --help clearly show this assist concept and exit
-f FILE, --file FILE APK file to scanning
-o OUTPUT, --output OUTPUT
Publish to file final results (NULL will be saved into random
file)
-p Pattern, --sample Sample
Path to customized patterns JSON
In general, if you you should not offer -o argument, then it will create final results file automatically.
Personalized designs can be included with the adhering to flag --pattern /path/to/policies.json to deliver sensitive search regulations in the JSON file structure. For example,
// procedures.json
"Amazon AWS Entry Essential ID": "AKIA[0-9A-Z]16",
...
$ python apkleaks.py -f /route/to/file.apk -c procedures.json -o ~/Documents/apkleaks-resuts.txt
Model
Latest variation is v1..2, and still advancement.
Credits and Many thanks
Given that this software incorporates some contributions, and I’m not an asshole, I’ll publically thank the next end users for their help and source:
- @ndelphit – for his inspiring
apkurlgrep, that’s why this instrument was produced. - @dxa4481 and y’all who lead to
truffleHogRegexes. - @GerbenJavado & @Bankde – for brilliant pattern to uncover URLs, endpoints & their parameters from
LinkFinder. - @tomnomnom – a
gfstyles. - @pxb1988 – for great APK dissambler
dex2jar. - @ph4r05 for standalone APK parser.