ActiveDirectoryEnumeration – Enumerate AD Through LDAP With A Collection Of Helpfull Scripts Being Bundled

ADE – ActiveDirectoryEnum
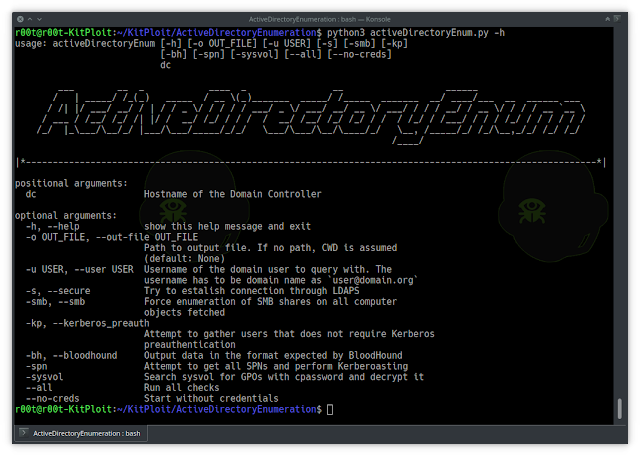
usage: activeDirectoryEnum [-h] [-o OUT_FILE] [-u USER] [-s] [-smb] [-kp]
[-bh] [-spn] [--all] [--no-creds]
dc
___ __ _ ____ _ __ ______
/ | _____/ /_(_) _____ / __ (_)_______ _____/ /_____ _______ __/ ____/___ __ ______ ___
/ /| |/ ___/ __/ / | / / _ / / / / / ___/ _ / ___/ __/ __ / ___/ / / / __/ / __ / / / / __ `__
/ ___ / /__/ /_/ /| |/ / __/ /_/ / / / / __/ /__/ /_/ /_/ / / / /_/ / /___/ / / / /_/ / / / / / /
/_/ |____/__/_/ |___/___/_____/_/_/ ___/___/__/____/_/ __, /_____/_/ /_/__,_/_/ /_/ /_/
/____/
|*----------------------------------------------------------------------------------------------------------*|
positional argu ments:
dc Hostname of the Domain Controller
optional arguments:
-h, --enable display this assistance message and exit
-o OUT_FILE, --out-file OUT_FILE
Route to output file. If no path, CWD is assumed
(default: None)
-u Person, --user Consumer Username of the area consumer to question with. The
username has to be domain title as `user@area.org`
-s, --secure Attempt to estalish relationship via LDAPS
-smb, --smb Drive enumeration of SMB shares on all pc
objects fetched
-kp, --kerberos_preauth
Endeavor to assemble customers that does not need Kerberos
preauthentication
-bh, --bloodhound Output info in the format envisioned by BloodHound
-spn Endeavor to get all SPNs and conduct Kerberoasting
-sysvol Look for sysvol for GPOs with cpassword and decrypt it
--all Operate all checks
--no-creds Start out devoid of credentials
Set up
Operate set up by means of pip3:
pip3 put in .Given that it is not yet dispersed via pip packages yet this is the way, for now. The script can now be named as a module or be imported:
python3 -m activeDirectoryEnum If you run BlackArch, ActiveDirectoryEnum is accessible through pacman as such:
pacman -S activedirectoryenumIntegrated assaults/vectors
- ASREPRoasting
- Kerberoasting
- Dump Advertisement as BloodHound JSON information
- Browsing GPOs in SYSVOL for cpassword and decrypting
- Operate without creds and try to assemble for even more enumeration all through the run
Collaboration
When this challenge is formulated to suit my need to have, any collaboration is appriciated. Remember to experience free of charge to fork the job, make variations in accordance to the License agreements and make a Pull Ask for. I only request that:
- Hold equivilent naming common as the foundation venture
- Hold equivilent syntaxing
- Check your code
- Mistake dealing with is included
- Doc the function – both equally in code but also for prospective Wiki web site
Many thanks & Acknowledgements
Major many thanks to the creators of: Impacket BloodHound BloodHound.py
With no the above this wrapper was not attainable.