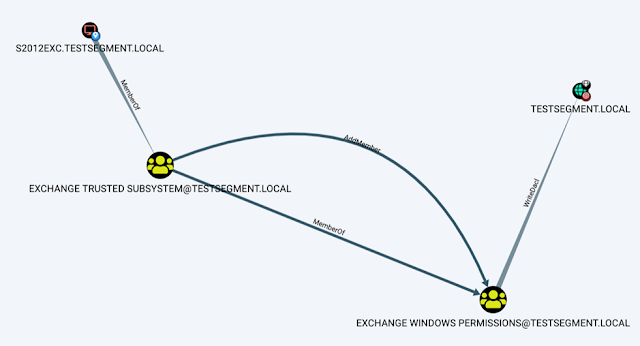
Aclpwn.Py – Active Directory ACL Exploitation With BloodHound

Aclpwn.py is a device that interacts with BloodHound to recognize and exploit ACL based privilege escalation paths. It can take a commencing and ending position and will use Neo4j pathfinding algorithms to discover the most successful ACL based privilege escalation path. Aclpwn.py is related to the PowerShell dependent Invoke-Aclpwn, which you can go through about in our site.
Dependencies and installation
Aclpwn.py is compatible with both Python 2.7 and 3.5+. It demands the neo4j-driver, impacket and ldap3 libraries. You can install aclpwn.py by way of pip: pip put in aclpwn. For Python 3, you will need the python36 department of impacket considering that the learn department (and versions released on PyPI) are Python 2 only at this issue.
Utilization
For usage and documentation, see the wiki, for illustration the quickstart website page.
Attributes
aclpwn.py at present has the subsequent functions:
- Immediate integration with BloodHound and the Neo4j graph databases (quick pathfinding)
- Supports any reversible ACL dependent assault chain (no help for resetting person passwords appropriate now)
- Highly developed pathfinding (Dijkstra) to find the most efficient paths
- Guidance for exploitation with NTLM hashes (move-the-hash)
- Will save restore point out, easy rollback of alterations
- Can be operate by using a SOCKS tunnel
- Written in Python (2.7 and 3.5+), so OS impartial
Mitigations and detection
aclpwn.py does not exploit any vulnerabilities, but relies on misconfigured (often mainly because of delegated privileges) or insecure default ACLs. To remedy these concerns, it is critical to identify possibly dangerous ACLs in your Energetic Listing ecosystem with BloodHound. For detection, Windows Celebration Logs can be used. The relevant occasion IDs are described in our site