FiddleZAP – A Simplified Version Of EKFiddle For OWASP ZAP
FiddleZAP is a simplified version of EKFiddle for OWASP ZAP.
With ZAP as your web proxy, you are able to flag malicious traffic based on predefined regular expressions.
Example: Alert, highlighting and tagging when a regex matches on a string within the HTML source code of a compromised website
Installation
-
Download and install ZAP: https://www.zaproxy.org/download/
-
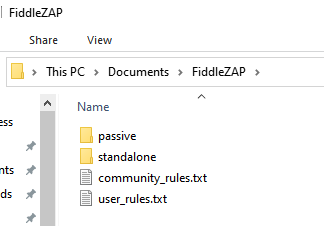
Download or clone the FiddleZAP directory into your Documents folder.
It should have the following structure:
There are 2 scripts (standalone, passive rules). The former is used to run manually on the currently loaded session (web traffic), the latter automatically runs while recording traffic.
Stand Alone
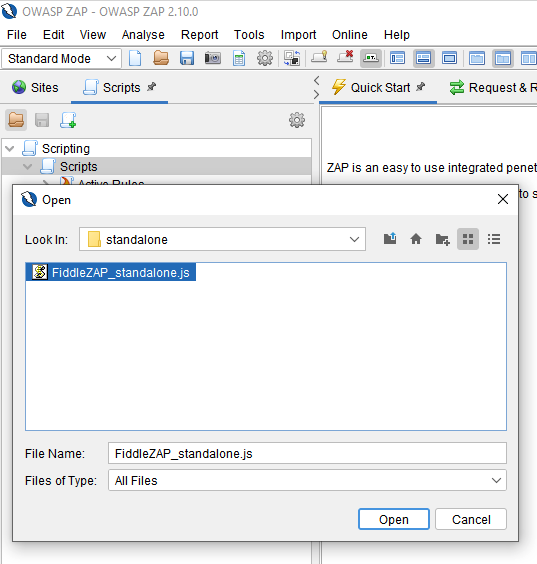
First, install the standalone script:
- Click on the Load script icon:
- Select the following parameters:
- It now shows under standalone:
Passive Rules
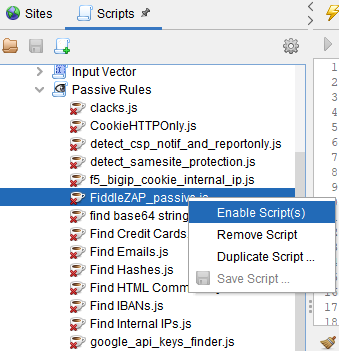
Next, install the passive rules script:
- Click on the Load script icon:
- Select the following parameters:
The FiddleZAP script should now show up under Passive Rules. If it is not enabled, right-click on it and select Enable script.
Features
Regexes (rules) to detect malicious traffic
Rules for FiddleZAP can look for URI patterns and source code patterns (session body).
-
A
community_rules.txtfile is provided with some examples. -
The
user_rules.txtis your own rules file.
Rules are automatically loaded and used to scan incoming traffic (if Passive Rules script is enabled). If you want to run rules on previously captured traffic, you need to run the standalone script.
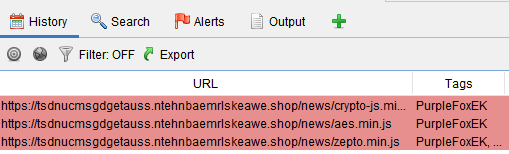
Color coding and tagging of matching web sessions
(This feature requires the neonmarker add-on)