Umay – IoT Malware Similarity Analysis Platform
IoT Malware Similarity Analysis Platform
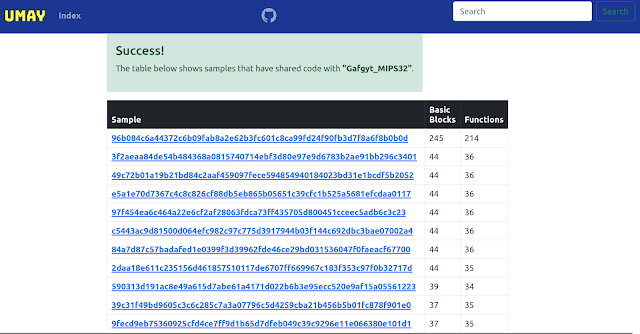
This project provides IoT malware similarity analysis based on shared codes. It helps to identify other malwares that have shared code with the analyzed file. In this way, you can have a chance to get an idea about the family of the malware. There are various devices with different architectures in the IoT ecosystem. Static-based methods are more effective when addressing the multi-architecture issue. 1000 malware binaries provided by IoTPOT were used in the project. The basic blocks and functions of each of binaries were extracted by radare2 and the hash values of these data were stored in the SQL database. The basic blocks and functions of the sample to be analyzed are query from this database and all malwares that have shared code are listed.
Current features
- Shared code based static analysis.
- Supporting ARM, MIPS, x86-64, i386, PowerPC, m68k, Renesas SH.
- ?
Getting Started
Prerequisites
- Python3+
- Radare2
- r2pipe
Installation
git clone https://github.com/mucoze/Umay
cd Umay
virtualenv venvsource venv/bin/activatepip install -r requirements.txtpython manage.py makemigrationspython manage.py migratepython manage.py createsuperuserpython manage.py runserverand now project app is accesible from your browser. Default: 127.0.0.1:8000
Create your own dataset file
python create_dataset.py samples/
Give the directory where all the samples are located as an argument and it will generate the dataset.db file for you.
🤝
Contributing
Contributions, issues, and feature requests are welcome!
Feel free to contact me.
License
Umay is licensed under Apache License 2.0