VECTR – A Tool That Facilitates Tracking Of Your Red And Blue Team Testing Activities To Measure Detection And Prevention Capabilities Across Different Attack Scenarios
VECTR documentation can be found here: https://docs.vectr.io
VECTR Community Discord Channel: https://discord.gg/2FRd8zf728
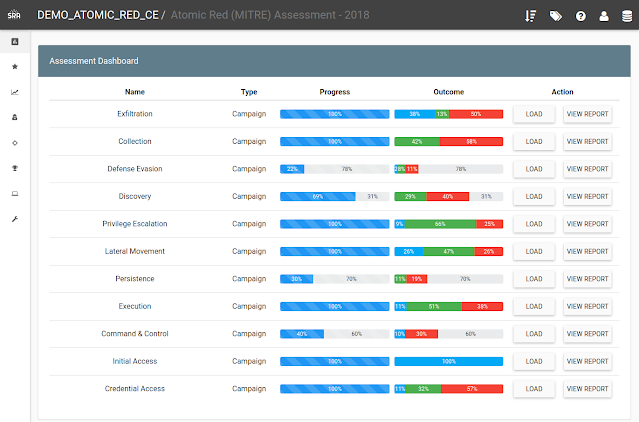
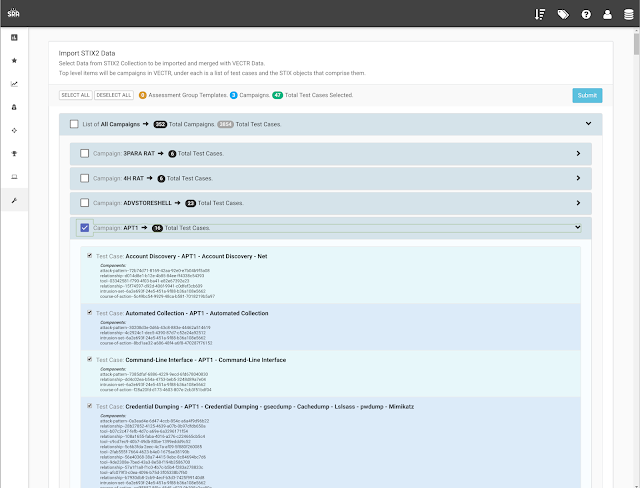
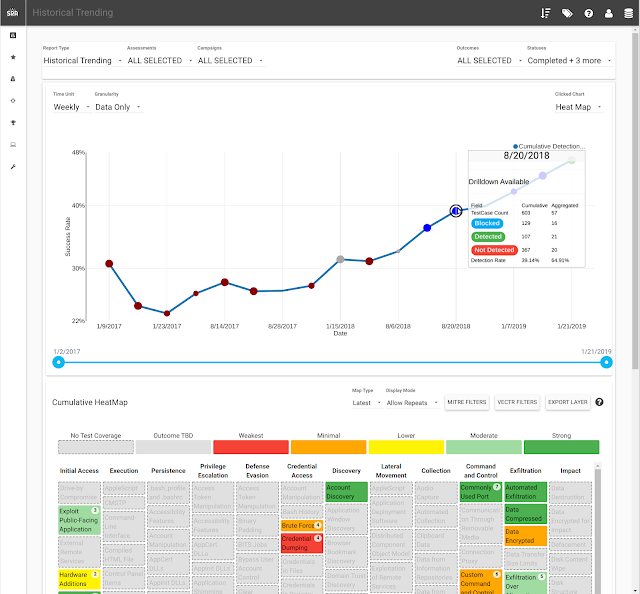
VECTR is a tool that facilitates tracking of your red and blue team testing activities to measure detection and prevention capabilities across different attack scenarios. VECTR provides the ability to create assessment groups, which consist of a collection of Campaigns and supporting Test Cases to simulate adversary threats. Campaigns can be broad and span activity across the kill chain, from initial compromise to privilege escalation and lateral movement and so on, or can be a narrow in scope to focus on specific detection layers, tools, and infrastructure. VECTR is designed to promote full transparency between offense and defense, encourage training between team members, and improve detection & prevention success rate across the environment.
VECTR is focused on common indicators of attack and behaviors that may be carried out by any number of threat actor groups, with varying objectives and levels of sophistication. VECTR can also be used to replicate the step-by-step TTPs associated with specific groups and malware campaigns, however its primary purpose is to replicate attacker behaviors that span multiple threat actor groups and malware campaigns, past, present and future. VECTR is meant to be used over time with targeted campaigns, iteration, and measurable enhancements to both red team skills and blue team detection capabilities. Ultimately the goal of VECTR is to make a network resilient to all but the most sophisticated adversaries and insider attacks.
Documentation
Feature Breakdowns By Release
VECTR v7.1.1 Feature Breakdown
Team
LEAD PROGRAMMERS:
- Carl Vonderheid
- Galen Fisher
- Daniel Hong
PROGRAMMERS:
- Andrew Scott
- Patrick Hislop
- Dan Guzek
- Zara Gunner
- Nick Galante
DESIGN & REQUIREMENTS:
- Phil Wainwright
DEV OPS:
- Paul Spencer
GRAPHIC DESIGN & MARKETING:
- Doug Webster
License
Please see the EULA
Atomic Red LICENSE